ControlMonkey solution for Terraform CI/CD acts as a quality gate for any changes performed to the infrastructure in the Git repository, so whenever someone pushes new code, we run a procedure called ‘Deployment’ that validates the code change and runs ‘Terraform Apply’, in case all tests pass successfully.
Today we are pleased to announce that we have enhanced our CI/CD solution with Approval Policies, an additional validation mechanism for any infrastructure change done in your Git repository.
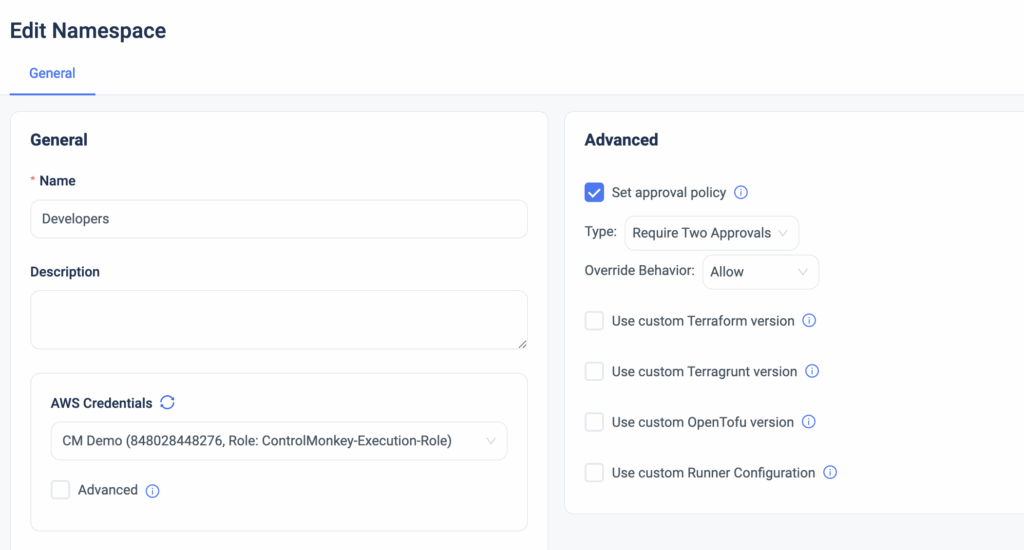
Starting today, ControlMonkey users can set approval policies that require the review of any requested infrastructure change.
These approval policies can be applied to a namespace or to a specific stack for that extra layer of granularity.
Setting approval policies introduces a manual approval step before the ‘Terraform Apply’ command actually runs. By default, Every deployment requires manual approval.
Types of approval policies:
- Auto Approve
- Require 1 approval
- Require 2 approvals
Changes to production are always risky, but with ControlMonkey Approved Policies, you can add an extra layer of control and prevent costly misconfigurations before every ‘Terraform Apply’ is executed.
Approval Policies are predefined and are available out of the box, so no manual policy writing is needed here.
Interested to learn how ControlMonkey streamlines every infrastructure change and helps companies like yours in their Day 2?
Our team is waiting to speak with you!

A 30-min meeting will save your team 1000s of hours
A 30-min meeting will save your team 1000s of hours
Book Intro Call
Sounds Interesting?
Request a Demo