IaC workflows with AI are emerging because Infrastructure as Code (IaC) alone made cloud changes repeatable—but not easy to review or safe over time. As Terraform environments scale, pull requests grow longer, reviews slow down, and critical context lives in people’s heads.
At the same time, manual fixes, emergency changes, and ClickOps introduce drift that erodes the guarantees IaC was meant to provide. Most teams only discover the problem after an incident or audit failure.
By adding context and guardrails into the delivery process, IaC workflows with AI help teams scale infrastructure without losing control.
Why Blend AI into IaC Workflows?
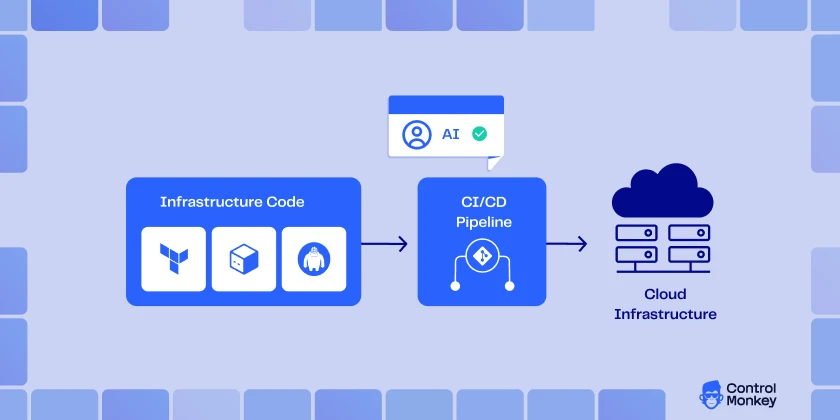
AI connecting to Infrastructure as Code (IaC) technology workflows is not about removing humans from production. It is rather focused on removing some of the mental load on the operator. With some supervision, AI-powered IaC, integrated with AI agents, can sit on top of the declarative code as a permanent reviewer. It flags risks, guides policy enforcement, and predicts blast radius. Provisioning of actual infrastructure is still integrated with existing CI/CD pipelines, GitOps flows and tools of IaC.
In the case of Traditional IaC, the still human is the one responsible for context interpretation of the risks. The reviewer, in the case of services and regions within a cloud provider, need to understand both cost and network exposure, access scope, data residence, and uptime. But AI can surface that context (cut right through that!). What is about to change, why does it matter, does it violate policy, and is there a clear rule to remediate that policy breach? So, large teams can go faster and safer by adopting IaC workflows with AI.
Key Advantages of an IaC Workflow with AI
These are the most immediate, high-impact ways AI improves how teams work with IaC today.

1. Plan explanation in plain language
Rather than reading a 200-line diff, reviewers receive a one-paragraph summary, which states that two subnets were created, one security-group rule was narrowed, and a new IAM role was created. The assistant describes, in layman’s terms (rather than just provider arguments), network configurations, network traffic exposure, and network access privileges.
It’s more than a convenience. Security, SRE, compliance, and even product owners understand what is going on. This decentralizes knowledge and accelerates onboarding, a core benefit of IaC workflows with AI.
2. Catching risky changes early
Changes can be vetted through policy-as-code and configuration-scanning tools, including OPA/Rego, Sentinel, Checkov, and Trivy’s IaC Checks. AI models can identify risky elements, offer safer alternatives that follow security best practices, and explain why the proposed code is problematic, all before code is ever committed to production. Most importantly, this is done before provisioning, rather than after deploying code and discovering an exposed bucket or an overly permissive IAM policy, where reviewers see the issue in a pull request.
3. Auto-generating compliant code
When you request a VPC, private subnet, or a new Kubernetes namespace, the assistant can create Terraform or Helm snippets using your specified tagging rules, naming conventions, and baseline security posture. This will reduce the copying and pasting of outdated modules and maintain standards across different teams and environments. Though the automated code will still get flagged for review, policy checks, and scanning, engineers benefit from starting with a solid template instead of having to build one from scratch.
4. Detecting and Fixing Drift with AI-Driven IaC Workflows
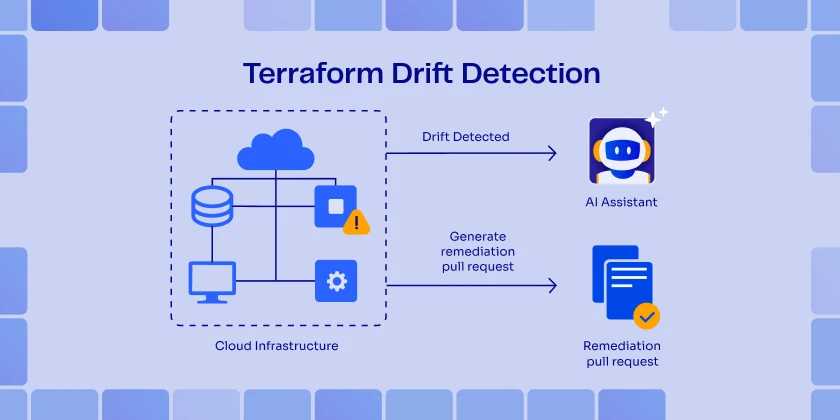
People start changing things over time. Someone is doing a quick fix for a role. Someone else opens a firewall rule. And another person is making a resource outside the workflow. Live infra state vs. IaC configuration can be compared. That is where AI suggests a `remediation pull` request, or it can be governed through reconciliations using your CI/CD or GitOps automation. When invisible drift leads to an incident at 2 a.m., it no longer drifts. Instead, it is now an actionable task in version control.
Why Traditional IaC Workflows Break at Scale
AI gives teams governance at scale. As infrastructure progresses through different geographies, tenants, and compliance zones, there’s no way for one engineer to recall all the exceptions, waivers, and patterns. An AI assistant can preserve some of that institutional knowledge. It becomes a perpetual reviewer who knows that some services, for instance, should never be publicly exposed at certain regions, or that a previous change introduced instability when a limit was raised.
The AI model also provides tracing. Every recommendation can be linked to a specific policy, past incident, or a cost model. Such explainability is key for audit, compliance, and trust, a major benefit of IaC workflows with AI. Instead of vague rejection, a violation of least privilege policy in a production namespace, which is also safer, can be offered as an explanation.
3 Core Principles for AI-Enhanced IaC Workflows
These principles define how AI should participate in your infrastructure workflow without taking unsafe direct control.
Collect context
To assist better, the assistant should have visibility over the IaC repositories, control state files, version control systems, assign tagging policies, review past incidents, and adhere to compliance policies. With sufficient context, it can exercise oversight and minimize human error as well as associate infrastructure with collateral services. That context also helps the AI identify the sensitive and experimental environments.
Reason before acting
Before any resources are created/destroyed, AI evaluates a pull request to analyze the blast radius, privilege changes, data exposure, and spend impact. It doesn’t silently mutate production. It has concerns and deliberate suggestions to mend the issues. This keeps engineers informed and active, enough to build trust with them.
Learn and adapt
Every accepted proposition informs the model. Over time, generative AI and ML models come to replicate the intuition of the best platform engineers. This translates to the junior contributors able to make changes more rapidly with a relatively lower risk, and the collective knowledge of the team is preserved through turnover.
End-to-End IaC Workflow with AI: Step-by-Step
This is how AI is integrated into the workflow instead of using it as a replacement.
Pre-commit scan
Long before a developer takes the request to the PR stage, the developer obtains feedback from a lightweight model or policy engine systematic review of diffs for obvious violations such as open security groups, overly permissive roles, tagged resources, public endpoints, and other risky or risky endpoints etc.. This cuts down on no-value back and forth and review performance bottlenecks.
Plan summarization
CI executes a terraform plan, or equivalent dry-run for kubernetes, or other cloud-native tooling. AI posts a concise summary of the pull request for resources to be created, modified, destroyed, and new roles that restrict access to sensitive data such as cluster-wide ConfigMaps or Secrets, and of what that means for the org’s security posture and compliance boundaries. This summary further ensures any auditing that is due is completed. Justifications for least-privilege policies are completed without the tedious evidence of policies gathering after the fact.
Interactive fix
If the AI flags something, engineers can respond conversationally. For example, reduce access scope to a specific namespace. The assistant then proposes a patch or follow-up commit. This tight loop compresses multi-day review cycles into minutes and gives newer engineers a safe path to correct misconfigurations in identity, networking, secrets, or ingress rules.
Human approval
Reviewers look at what the AI makes and approve it once they glance at the draft and see it does the changes they want. Most look at the visual and alignment design and not the small stuff like indentations and naming. The resource changes control version history, and there is no unmanaged change resource through back windows.
Post-merge monitoring
In case someone changes roles, or explicitly opens a production firewall rule, the assistant might fire an alert and append a pull request. This is self healing and infrastructure is securely delivered. It does change production but it also automatically creates proposals that get sent through the organization’s infrastructure which they already trust.
Operational Outcomes of an IaC Workflow with AI
These are the measurables teams typically see after integrating AI into the IaC workflow.
- Speed without Chaos – Pull request cycle time decreases due to AI completing repetitive reviews, boilerplate fixes, and gathering context. This leads to quicker environment spins and unblock sooner deployment of applications so that features can be delivered to the customer sooner.
- Reliability by Default – If drift was extinguished and closed ad-hoc incidents are doing fixes, incidents themselves drop. Workflows powered by AI can detect and isolate configuration drift to mitigate and defend incidents of unengifted security.
- Security that Scales – Shadow infrastructure is negated to stop the creation of unedged policy guardrails. These are stable and only declared, tagged, scanned, and reviewed through the managed pipeline.
- Instant Up-skilling – New hires no longer learn every rule of the platform. The assistant describes the risk, how to mitigate, and the company pattern to follow. This decreases the time more senior engineers spend explaining the rules and instead allows optimizing more. It reduces costs by improving the visibility of costly instance types or unnecessary public endpoints during the reviews instead of after.
Implementation Roadmap
Here is how many teams carefully implement AI without going off the rails.
- Pick a low-risk pilot – Start with either a single repository or a single shared layer like networking or identity. This validates values with low blast radius. It also gives the team a chance to set expectations. Who AI can suggest and who can override and how are those escalations managed?
- Wire up context sources – Assistants should have a read-only privilege to relevant repos, policy state files, policy definitions, tagging and cost templates, and rules. Stick to the least privileged model. The focus is solely to let the AI analyze and recommend, not provision, and to make sure sensitive information in state files is either blanked out or managed in a secure way.
- Define success – Measure pull-request turnaround times and rollbacks, total cloud spend, on-call noise. If on-call infra sees fewer urgent pinging due to the system mitigated infra misconfigurations pre-deployment, that’s of big value.
- Iterate openly – Grant engineers score or reply to AI’s comments. The event would be like treating the AI miss with a teammate who is inexperienced. This tighter feedback loop is beneficial for aligning the model on how the platforms operated, and not just the generic best practices.
To keep things convenient, most current integrations handle GitHub, GitLab, or Bitbucket, which means AI can function in the form of comments, summaries, or proposed changelists in the engineering tools already in place, making the onboarding process painless, as there’s no need to implement some new management tool.
IaC Workflow with AI: Challenges & Mitigations
These are the usual reasons when teams try bringing AI for the first time for workflow automation.
Data privacy
Plans around Infrastructure as Code and states can reveal sensitive infrastructure information like resource names, ARNs, IP ranges and other credentials, especially if teams are not careful. When it comes to sensitive environments, organizations should prefer on-prem, or single tenant deployments for AI assistants and should sanitize or scope what is shared with AI. Periodic security audits are still very important.
Legacy snowflake stacks
If any portion of your platform is still being managed manually or put together with custom scripts, AI cannot reason about these components. The fix is small step standardization: refactor a single module or service at a time to consistent, reviewable Infrastructure as Code. Proposing refactors is something Generative AI can help with, but the migration path needs to be chosen by a human.
Model drift
Your infrastructure is not static. New regions, new compliance policies, new runtime stacks, new naming policies, new tagging policies, these all lead to old assumptions degrading over time. The assistant needs to be retrained or the guiding rules changed otherwise it cannot remain helpful. AI tuning should be treated like any other piece of platform maintenance.
Future Directions for IaC Workflows with AI
Big cloud providers now have LLM interfaces that can handle IaC plans and state. Many teams are already translating Terraform plans and interacting with Kubernetes state and controllers into normalized JSON and feeding these into AI and policy engines. There are open source advancements in tool chains that handle plan summarization and policy and impact analysis that are becoming more visible. These result in pull requests with an interactive impact graph, least-privilege assessments, and remediation ready diffs.
The future of IaC workflows with AI is human-approved automation, not autonomous mutation of production. It’s AI crafting changes that are contextually safe and explainable and need only a human stamp of approval. That preserves the lockdown on reliability, compliance, and budget, but provides teams that have been starved the acceleration they need.
Conclusion
We are not trying to take DevOps or platform engineers jobs. We are trying to automate repetitive tasks, highlight hidden risks, and interpret the intention behind the infrastructure. An AI can help make Infrastructure as Code faster, safer, and less stressful by understanding your entire cloud footprint, reasoning before taking action, and learning from every merge.
When AI is integrated into delivering an IaC (Infrastructure as Code) workflow, it is about trust. It is about the trust of gained consistency and predictability from IaC—now AI empowers it with context, control, and velocity. The outcome is cleaner reviews, better posture on security, fewer incidents, faster delivery without grip of production control. If faster reviews, better security, and zero-drift environments are what you desire, it is time to bring an IaC workflow with AI into operation. Experience ControlMonkey and get governed automation over your cloud.