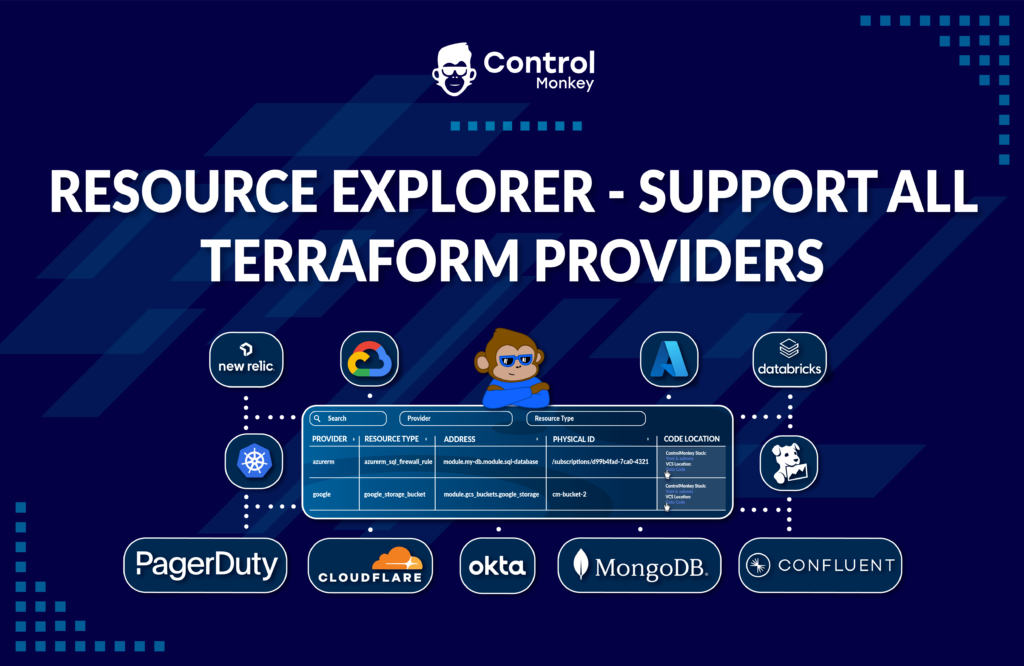
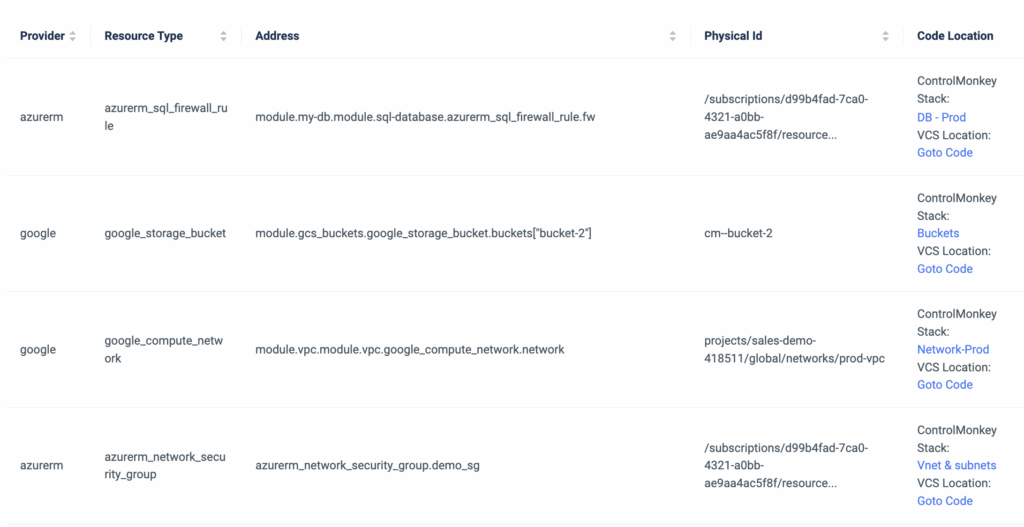
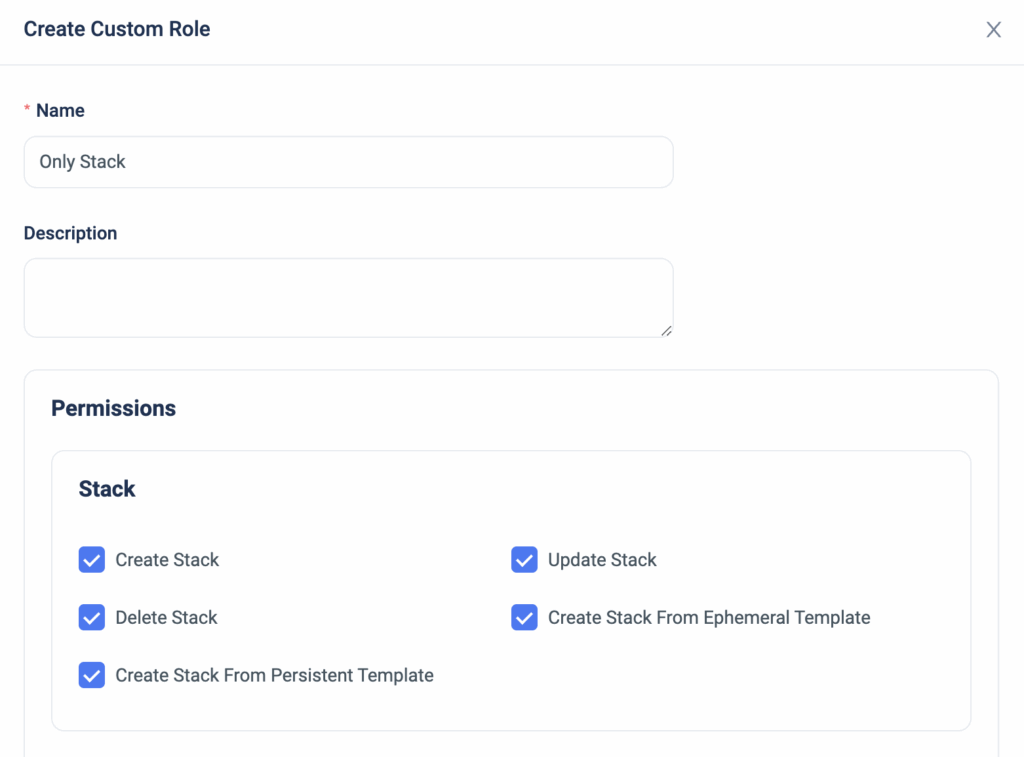
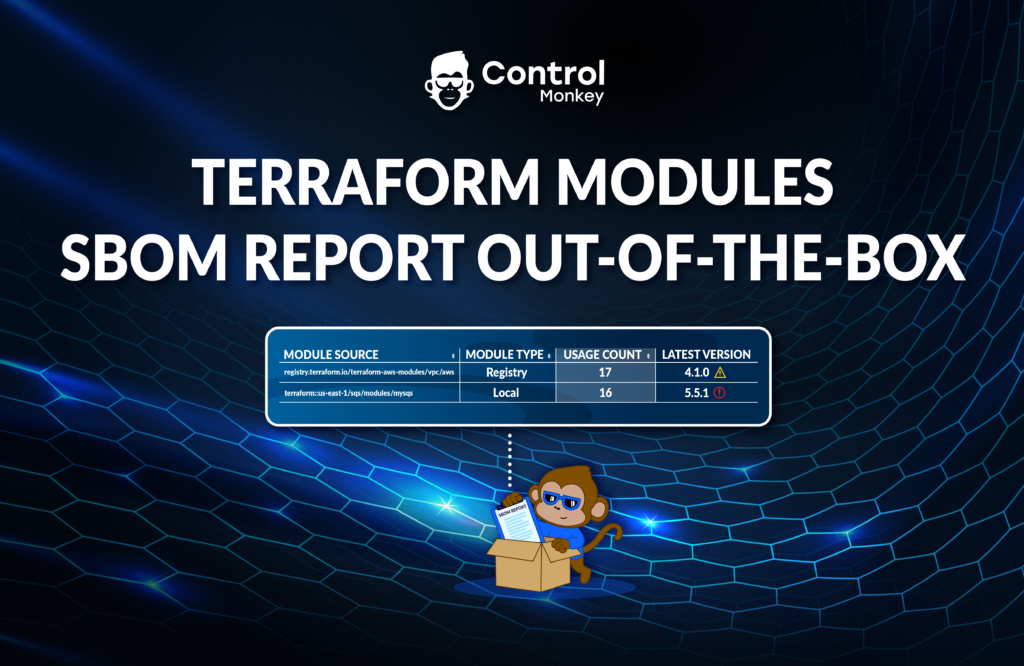
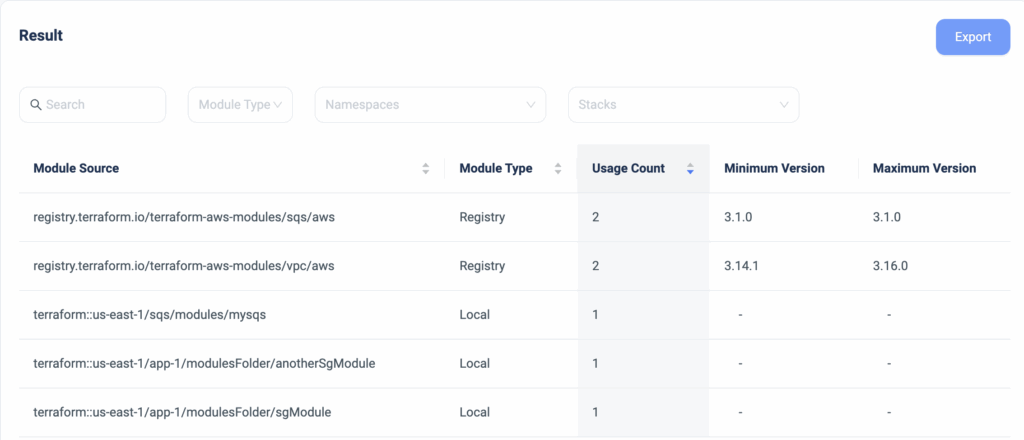
Today, we are pleased to announce the release of ‘Remote Plan from Local Machine,’ the latest enhancement to our Terraform CI/CD engine.
How do your cloud engineers properly test their Terraform code changes before committing to Git and getting feedback without running a PR?
There are a few challenges there:
- The Secrets and variables their code requires are unavailable on their local machine and shouldn’t be for security reasons.
- They don’t have the organization’s guardrails and policies to test their local code.
Up until now, users had to commit the code, create a PR, and then get the needed feedback from their centralized Terraform pipeline. This process, of course, slowed down the pace of development and created a lot of “waiting time” between each code update and PR inspection.
Today, we’re happy to announce our “Remote Plan from Local Machine” capability, where cloud engineers can test their Terraform Code changes locally without initiating a full PR and pushing the GIT code.
Remote Plan enables you to run your ‘Terraform plan’ locally by triggering a plan simulation remotely on ControlMonkey and getting feedback on the plan’s output.
The integration is pretty easy. All you have to do is run the ‘terraform login api.controlmonkey.io’ command:
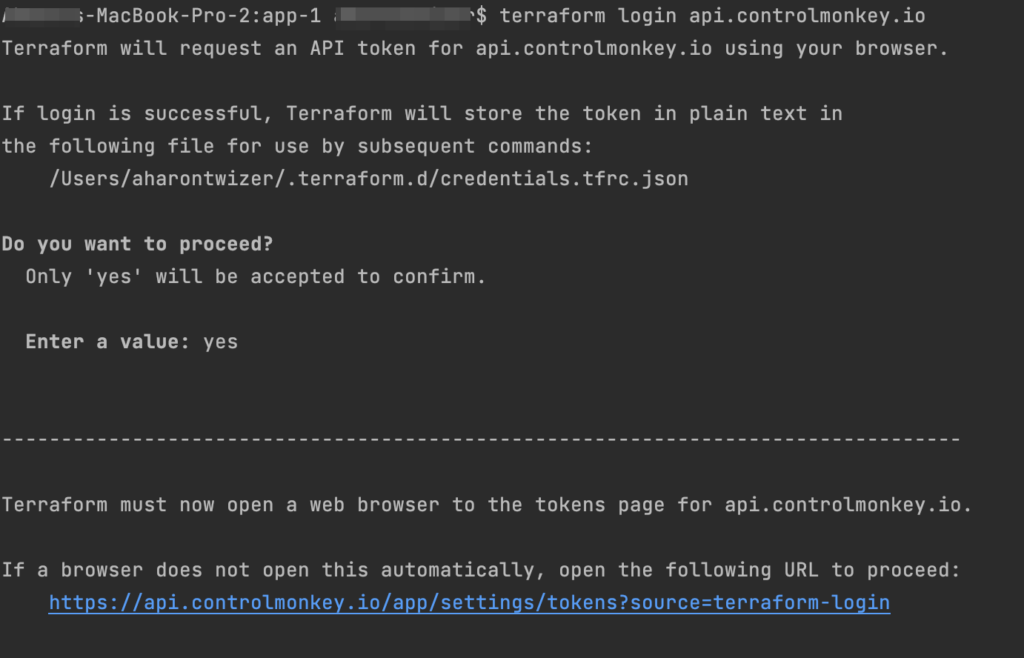
And then you can work as you’re used to, running ‘terraform plan’ commands on your local machine:
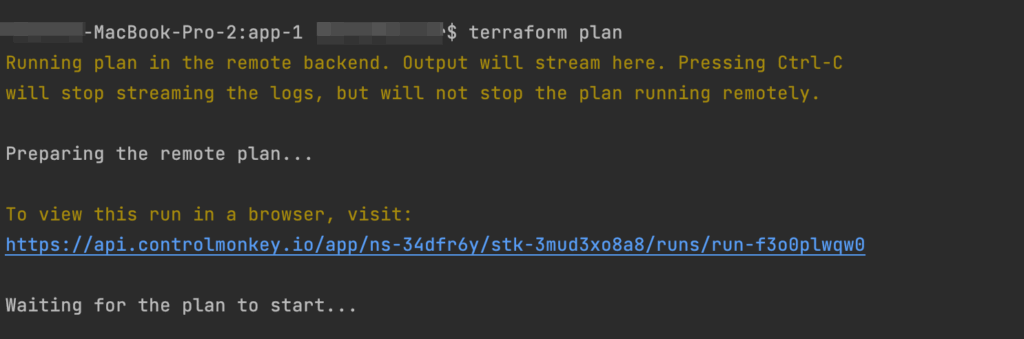
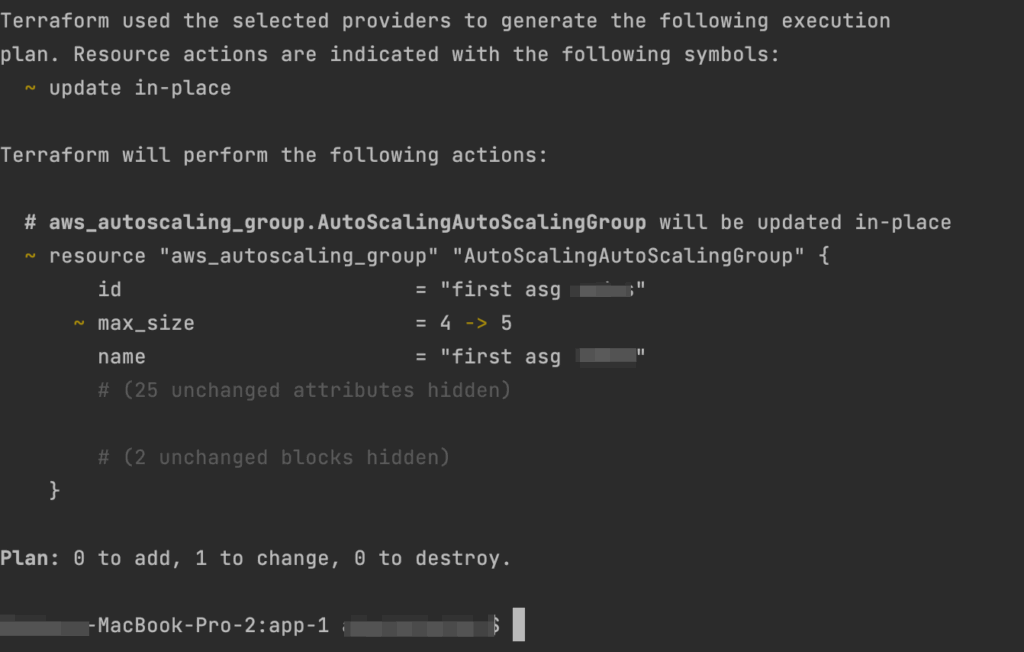
It uses your local Terraform files but actually runs it remotely in ControlMonkey, using the shared state and your environment’s variables and secrets. Every Remote Plan triggers a Plan in ControlMonkey, so you will have the full audit also on the ControlMonkey console:
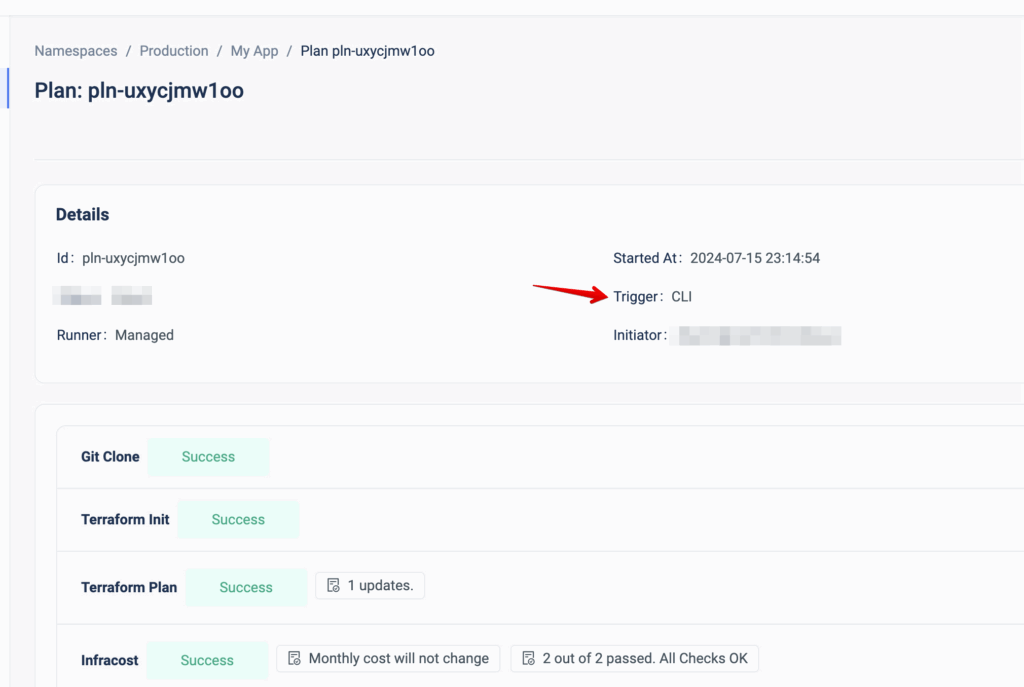
By running a remote plan, your engineers can build faster and test their changes locally before committing to them.
Are you managing Terraform at scale?
Our Experts are available for a quick call so you can learn more about the future of Terraform Automation and how it can benefit your team.