Your DevOps team might be practicing ClickOps without even realizing it causing inefficiencies, misconfigurations, and cost sprawl.
Manual, UI-based cloud management processes that bypass Infrastructure as Code (IaC) principles—or worse, in the absence of IaC—lack the rigor to manage complex cloud environments. These ClickOps processes slow down deployments. They also increase errors and create compliance risks. They make scaling harder and decrease the reliability of the infrastructure. This can lead to higher costs. Switching to an automated IaC-based system can help find and remove ClickOps. This change can also boost efficiency and the business value of a company’s cloud infrastructure.
What is ClickOps?
ClickOps is the term of art used to describe instances or ongoing practices where cloud infrastructure engineers—often members of the DevOps team—make manual changes to the infrastructure (large and small) via their computer. They do this by clicking into the company’s portal to create, edit, or delete resources.
Engineers and others may see ClickOps as an easier way to make changes. It uses less code and is more accessible. This is especially true for users with access but who lack expertise in infrastructure provisioning or application deployments. Beyond convenience or lack of technical skill, other common instances where team members may choose ClickOps:
- They lack automation tools or system skills,
- While in the midst of firefighting urgent issues,
- Or during the changeover of a merger or other types of reorganizations.
Examples include:
- Making infrastructure changes via the AWS Management Console.
- Altering security groups in the cloud platform.
- And any other occurrence of manual provisioning rather than an IaC automation tool such as Terraform.

A cloud DevOps engineer logs into the cloud provider’s interface. They manually choose the settings for a new virtual machine or allocate new storage space. A cloud security engineer sets up or changes a security group. Another DevOps engineer in a different location is making a similar change. They are creating a new role and setting permissions.
When you think about managing a diverse and growing cloud environment, the options for DevOps are nearly endless.
Six ClickOps Hidden Risks
As you may have noticed from the examples above, with individual engineers making small or large manual changes to the infrastructure, the risk of unintended outcomes is considerable. Let’s take a look at some examples:
1) Productivity Drain
Manual work slows down deployments and management tasks.
Consider the employee who wants to manually create a new Amazon Elastic Compute Cloud (EC2) instance. This may seem convenient and even preferable to managers. However, what if they need to create 20, 30, or even 100 instances? Or consider the productivity drift when you have a diverse array of engineers making ClickOps changes for a range of needs across a complex cloud environment.
Each of these employees must work across multiple clouds and sift through cloud provider documentation to complete these tasks. Additionally, employees may have to do some of this work via generate-and-test due to UI updates or uncaptured documentation revisions. And the organization loses this knowledge acquired by significant effort on new employees because the experienced employee leaves the company or team.
2) Lack of Repeatability
There is no audit trail or version control. In manual ClickOps environments, it is hard to keep a clear record of who did what and when. This opaqueness can also lead to confusion and complications, especially when trying to firefight an urgent issue.
3) Increased Human Errors
As the above implies, ClickOps leads to misconfigurations. Human error is always possible—perhaps probable—even among the most experienced engineers and these errors can manifest themselves in a cloud architecture. These errors can cause the loss strategic performance benefits, downtime, and constant bug hunting or even disaster recovery efforts.
4) Compliance and Security Risks
The chaotic environment that ClickOps potentially create makes it harder to meet security policies and goals. For example, ClickOps might skip security controls set by the organization. It may not go through the same review and validation processes as those in an IaC system.
5) Drift from IaC
Even organizations that use automated Terraform solutions may still face ClickOps. This can lead to configuration drift, broken automation pipelines, and other issues. The more ClickOps the likelier the cloud infrastructure can diverge from its preferred state.
6) Cost Sprawl
ClickOps has the potential for profound cost implications due to:
- Burdens of manual processes,
- Need for repetitive tasks,
- Lack of automation,
- Inconsistent configurations,
- Scaling challenges,
- Increased risk and errors,
- Bug hunting,
- And rolling back changes if needed.
How to Identify ClickOps in Your DevOps Team
The main point is that the company’s engineers use ClickOps as the main way to manage cloud resources. They do this because they have not adopted IaC with an automated Terraform-aligned solution.
However, there are less obvious instances. For example, after a lift-and-shift to the cloud as the result of a merger or acquisition, engineers make some ClickOps changes because they seem small, convenient, and harmless. These then go unnoticed until the cloud infrastructure begins to go sideways.
Other clues include:
- Engineers frequently use cloud consoles instead of an automated solution.
- Frequent configuration drift issues.
- Lack of version control or automation in infrastructure changes.
- Increased time spent on troubleshooting misconfigurations.
- Compliance teams struggle to track infrastructure changes (who did this, when, and why?).
Five Best Practices to Transition from ClickOps to Automation
ClickOps and their related risks and challenges do not have to be a fact of life. The following offers a practical high-level guide:
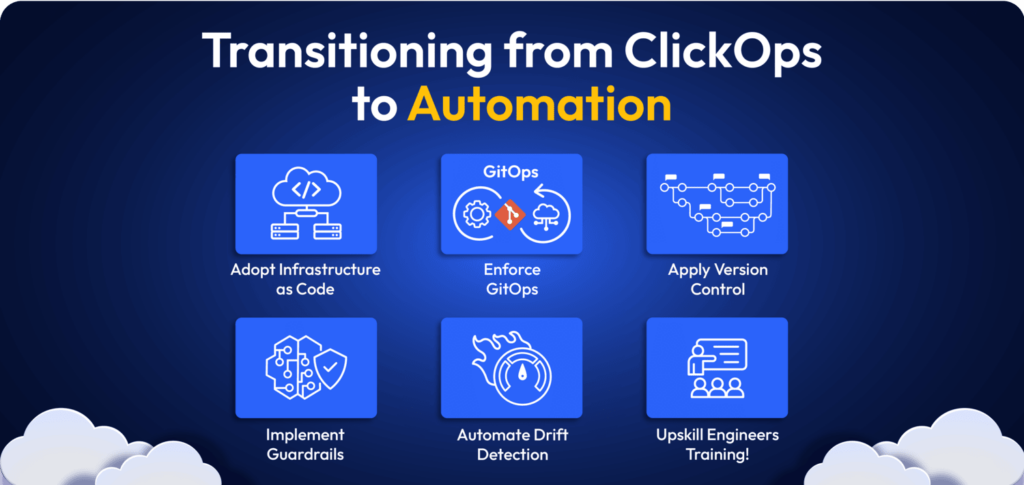
Adopt Infrastructure as Code:
With Terraform, Pulumi, or AWS CloudFormation you can define and manage resources effectively and efficiently. Deployments and other changes are automated and performed according to a defined set of security and management policies. Adjustments, such as updating resources, are a matter of updating parameters and initiating the deployment pipeline.
Further, these automation tools ensure there is standardization, consistency, repeatability, dependencies management, collaboration, scalability, and version control.
Enforce GitOps (single source of truth) & Version Control:
First, store all IaC code in a version control system such as Git to track changes, collaborate, and rollback changes if needed.
Second, all changes to infrastructure must follow a policy. These changes go through Git Pull Requests. The Git system captures and merges proposed changes from the DevOps team. This process helps with collaborative code review and discussion before integrating the changes.
Implement Guardrails:
Use policy-as-code tools like ControlMonkey Terraform CI/CD, Open Policy Agent (OPA), Sentinel, or AWS Config to consistently apply rules across all cloud platforms to prevent gaps or conflicting standards. These tools can find issues such as unused or underutilized assets, ghost assets, and ensure that organizations do not deploy non-compliant resources.
For example, ControlMonkey Terraform CI/CD Required Tag control policy enables an organization to create a rule that all resources have specific tag keys and tag values. Therefore, if a proposed change contains a resource without these tags, ControlMonkey’s CI solution will block it.
Allowed Regions control policy empowers an organization to define allowed regions in which an employee could spin up (quickly activated) a resource. If an employee attempts to spin up a resource in a non-allowed region, the allowed regions control policy will block it.
Automate IaC Drift Detection:
Drift means differences between what the organization wants for its infrastructure and what is actually deployed. This is defined by its IaC configuration. This can occur as organizations scale their infrastructure and/or have a complicated cloud environment they are trying to manage via manual or partially automated processes, with conflicting tools, or external dependencies.
Automation helps teams identify and tackle discrepancies to bolster security, compliance, functionality, and reliability. These capabilities help the organization align its intended state of the infrastructure to its actual state. For example, ControlMonkey’s Drift Detection algorithm performs regular checks to detect infrastructure drifts and prioritizes them based on severity and source.
Upskill Engineers:
Be persistent in training the organization’s teams on automation-first methods. This will help eliminate ClickOps practices at their source and prevent IaC drift.
How to Handle Brownfield Cloud Environments
Most cloud teams operate in brownfield environments, not greenfield ones—and that makes ClickOps even harder to unwind. If your infrastructure grew organically through years of console changes, the shift to Infrastructure as Code can feel overwhelming.
The key is to avoid big-bang rewrites and instead adopt a pragmatic migration path: start by identifying high-risk or high-change resources, use tools like terraform import or OpenTofu’s import capabilities to gradually bring those resources under code, and establish Git-based workflows moving forward.
This approach lets teams regain control incrementally while reducing drift and operational risk along the way.
How ControlMonkey Stops ClickOps
ControlMonkey closes that gap by giving cloud teams real-time visibility into every manual action across AWS, Azure, and GCP. With the ClickOps Scanners, you immediately see who changed what, when, and on which resource — even if it was done directly in the console.
Once a console change is detected, ControlMonkey ties it back to the exact drift it caused, so teams can fix issues fast instead of digging through logs or guessing. Every ClickOps event becomes part of a complete audit trail, giving you clear accountability and eliminating blind spots.
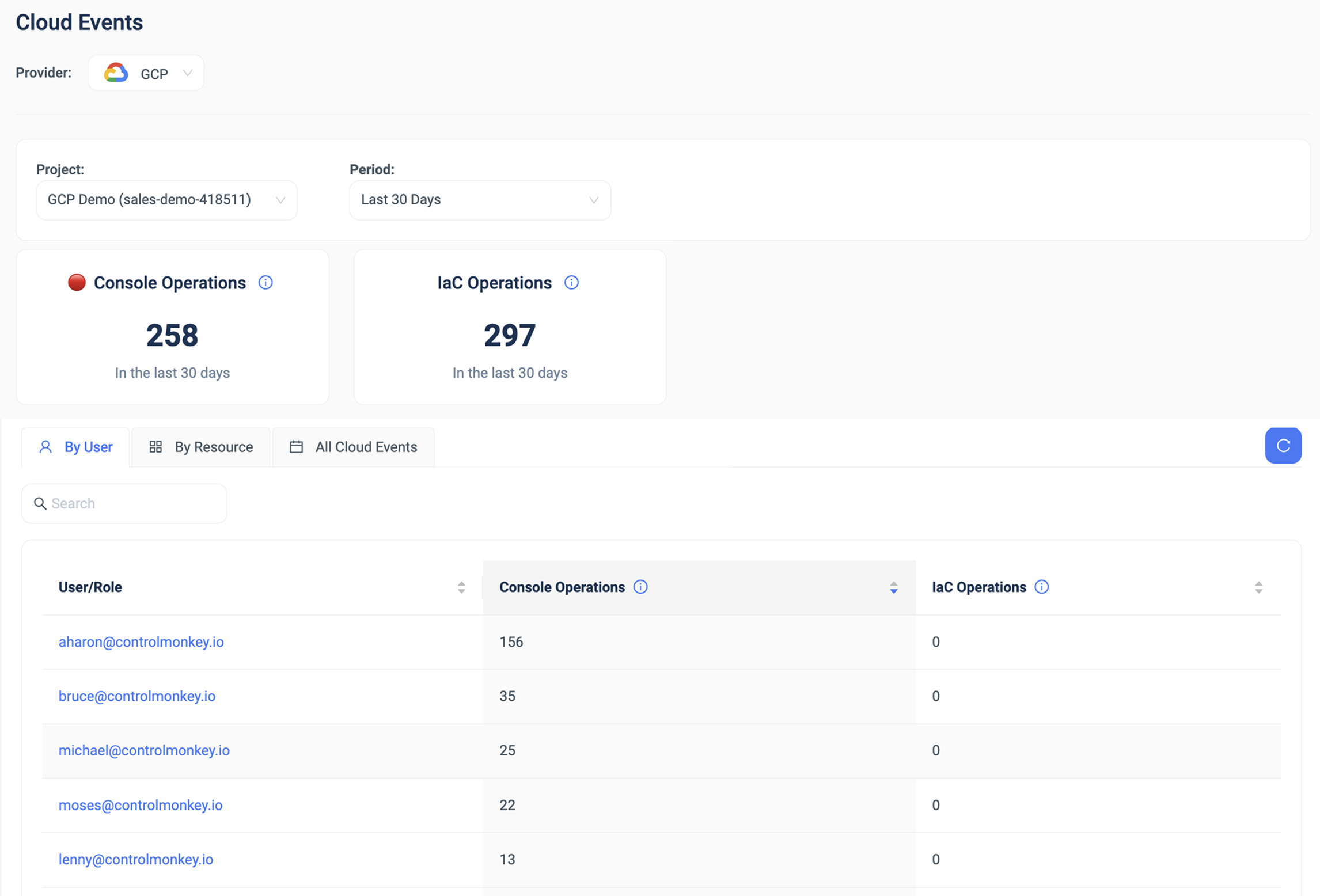
Beyond detection, ControlMonkey helps prevent ClickOps from happening again. With full cloud-vs-code inventory, import workflows for bringing unmanaged resources under Terraform, and guardrails that enforce Git as the single source of truth, teams move toward an IaC-only operating model without breaking existing environments.
The result: no surprises, no hidden changes, and no more “why did this break?” moments. Just total, enforceable control over how infrastructure changes are made.
The ClickOps Bottom Line
ClickOps is a hidden productivity problem. It leads to rising costs, creates risks, and causes compliance issues. This undermines the role of infrastructure as a center for creating strategic value.
Therefore, it is incumbent upon leaders to take a proactive stance by implementing IaC and automation practices to eliminate the practice of and impacts of ClickOps. So, if you suspect that ClickOps is undermining the value of your cloud infrastructure, creating inefficiencies, and negatively impacting costs, audit the organization’s workflows today and take the first step toward true cloud automation. Ready to fight ClickOps and Drifts? Feel like your infrastructure need help to scale it management? Book a demo with ControlMonkey today to see how our platform can streamline your Terraform workflows.






