Infrastructure as Code (IaC) has become the backbone of scalable cloud operations. But without standardization, teams risk ending up with duplicated scripts, inconsistent configurations, and slow rollouts. That’s where OpenTofu modules come in. OpenTofu – a community-driven fork of Terraform—lets DevOps teams build reusable, modular infrastructure stacks that are easy to version, scale, and maintain.
Much like the Terraform Registry the OpenTofu Registry helps teams discover and share standardized modules across environments. It’s designed to accelerate IaC adoption by making best-practice modules easily accessible—without reinventing the wheel.
In this guide, you’ll learn what OpenTofu modules are, how to structure them, and why they’re critical for clean, efficient IaC workflows.
Introduction to OpenTofu Modules – Basic Definition and Purpose
Any configuration directory containing the OpenTofu configuration file is a module. For example, the configuration directory is called aws-instance in our local machine, and this directory has OpenTofu configuration files that are used to create an EC2 instance in AWS. Since we can run OpenTofu commands from within the directory directly, this configuration is known as the root module.
Modules can call another module, which allows resource configurations to be packaged and reused. Modules are reusable blocks of configuration that define a specific piece of infrastructure or application configuration. A module will usually contain input variables, configuration logic, and output values to allow users to manage and configure infrastructure in a standardized way. Modules can declare infrastructure elements such as virtual machines, networks, databases, etc. Because the infrastructure is composed of modules, you can keep your codebase organized and easy to manage. The modular approach allows you to use the same setups across multiple environments with the aim of avoiding duplicated code.
Here’s a real-world use case. Create a reusable module to provision virtual machines across environments. Instead of copying the same code every time that you provision a virtual machine, you can use this module multiple times and parameterize the input for every environment.
Benefits of OpenTofu Modules: Faster Deployments & Clean Code
Using OpenTofu modules provides lots of benefits that contribute to cleaner code and faster deployments. Some of the key advantages include:
- Standardization ensures consistency across environments. OpenTofu modules standardize configurations across environments by embedding best practices.
- Less duplication means writing infrastructure code once instead of copying and pasting. Avoid code duplication by using modules with customizable parameters. This approach minimizes configuration errors and keeps your codebase maintainable.
- Easier collaboration allows developers to write code and manage their own modules, and the rest of the team members can use them in their own work.
- Environment-specific customization is you can make parameterizable modules with input variables to reuse the same module across many environments with different configurations. You can, for example, use a virtual machine module with different sizes or regions for the dev, staging, and production environments.
How Modules Work in OpenTofu – Structuring and Referencing Them
OpenTofu modules are structured in source files that establish infrastructure resources. They are composed in HashiCorp Configuration Language (HCL) and contain logic to configure the resources. To use OpenTofu modules, import them in your main configuration file by specifying the source. Modules can be imported from files on a local computer, from a Git repository, or the OpenTofu Registry.
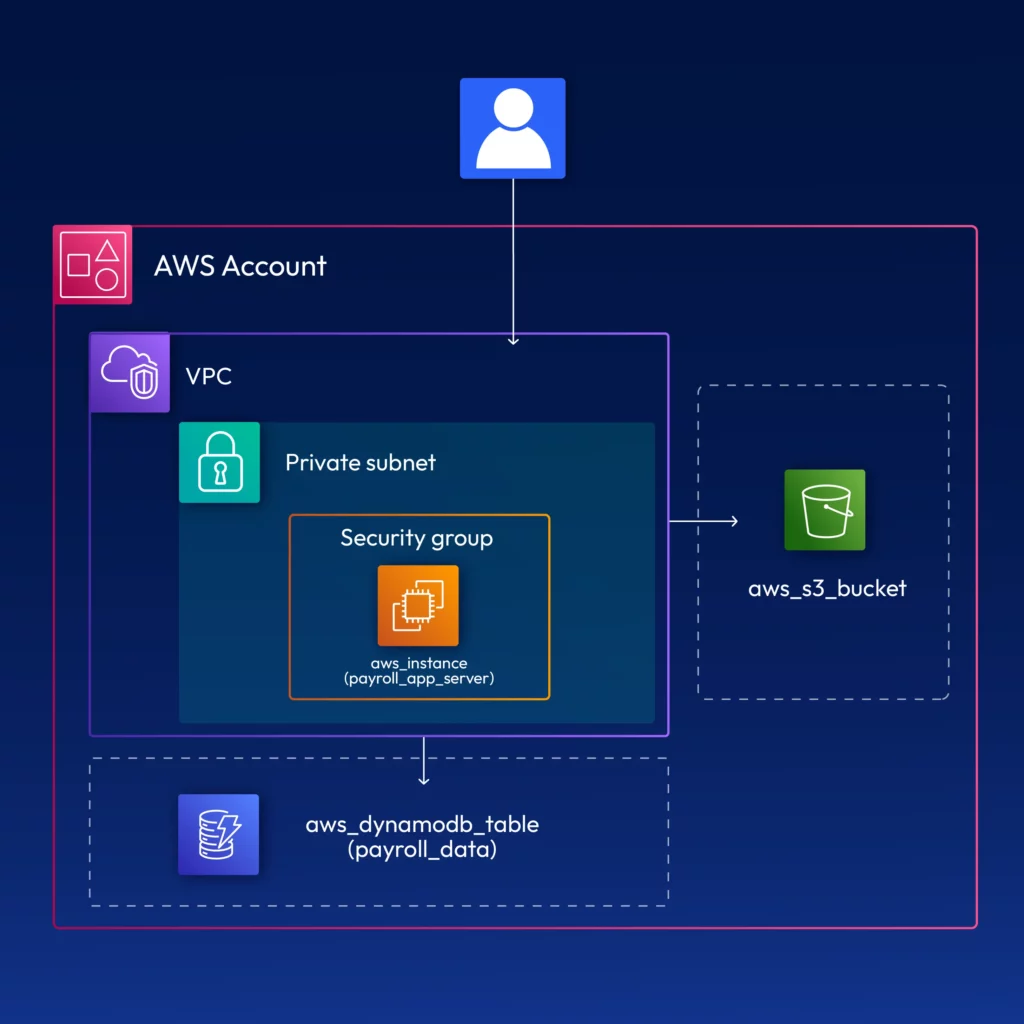
For example, ABC company has payroll software and wants to implement it in different countries and regions. Each country will have its instance of software deployed on the AWS cloud using the same architecture. It has a single EC2 using the custom AMI to host the application server. DynamoDB NoSQL DB will be used to store the employee and payroll data. The S3 bucket stores the pay stubs, tax forms, and other documents. So, we need to create a reusable OpenTofu module and use it to deploy the same stack of resources in different regions.
Architecture diagram for the example:
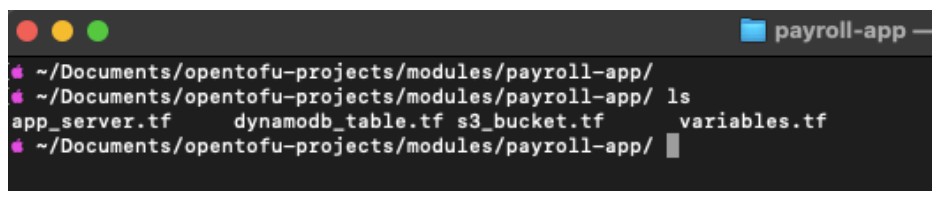
Create a new directory for the module codes. This is where the place to store all our reusable modules. Inside this, we have the reusable block for all the required services like EC2, S3, and Dynamodb.
AWS instance configuration (app_server.tf):
resource "aws_instance" "app_server" {
ami = var.ami
instance_type = "t2.medium"
tags = {
Name = "${var.app_region}-app-server"
}
depends_on = [
aws_dynamodb_table.payroll_db,
aws_s3_bucket.payroll_data
]
}S3 bucket configuration (s3_bucket.tf):
resource "aws_s3_bucket" "payroll_data" {
bucket = "${var.app_region}-${var.bucket}"
}DynamoDB table configuration (dynamodb_table.tf):
resource "aws_dynamodb_table" "payroll_db" {
name = "user_data"
billing_mode = "PAY_PER_REQUEST"
hash_key = "EmployeeID"
attribute {
name = "EmployeeID"
type = "N"
}
}Variables Configuration (variables.tf):
variable "app_region" {
type = string
}
variable "bucket" {
default = "flexit-payroll-alpha-22001c"
}
variable "ami" {
type = string
}Deploy the application stack in the us-east-1 region using the following structure. After creating another directory, us-payroll-app, and inside the directory, create a main.tf file.
$ mkdir /root/opentofu-projects/us-payroll-app
main.tf provider.tfModule configuration in main.tf:
module "us_payroll" {
source = "../modules/payroll-app"
app_region = "us-east-1"
ami = "ami-24e140119877avm"
}Use the OpenTofu commands below to create resources using the OpenTofu module.
tofu init
tofu plan
tofu applyBest Practices for Using Modules
Naming Conventions
Modules and resources should be given clear, descriptive names. This will allow anyone who utilizes the module to immediately understand what the module does. For example, name your modules according to the infrastructure component they deploy, like vm-module or networking-module.
Versioning
Pin your module versions to avoid breaking changes during upgrades.
module "vm" {
source = "OpenTofu/controlmonkey-vm-module/ec2"
version = "1.0.0"
}Module Structuring
Structure your modules in function-wise directories. For example, you can have a separate network, compute, storage directories, etc. Every module must be independent and manage one resource or a set of resources.
Inputs and Outputs
Keep input variables dynamic. Avoid hardcoded values—use variables to enable flexibility. Make them variables instead and allow users to customize them. In the same way, record the output of your module so that users are aware of what information is available for them after using the module.
Conclusion – Build Faster and Smarter with Reusable OpenTofu Modules
OpenTofu modules simplify cloud infrastructure deployment and management. Using standardized, reusable modules, you can reduce duplication, speed up the deployments, and enhance team collaboration. With access to a large library of existing pre-build modules in OpenTofu Registry, you can get started quickly and build smarter, more efficient infrastructure.
Ready to modularize your infrastructure with OpenTofu and Terraform? Try ControlMonkey to automate deployment, enforce policies, and eliminate drift—at scale. – an IaC automation platform that brings automation deployments and can support you on that journey.

A 30-min meeting will save your team 1000s of hours
A 30-min meeting will save your team 1000s of hours
Book Intro Call
Sounds Interesting?
Request a Demo