When you use the AWS Provider, you can handle large deployments. You can break infrastructure definitions into reusable and easy-to-maintain modules.
Terraform is widely used to manage cloud infrastructure as code. It works by using providers, which connect Terraform to different platforms like AWS, Azure, and others. One of the most common providers is the Terraform AWS Provider. It lets you create and manage AWS resources from your Terraform files.
If you’re running Terraform on AWS, this provider is what makes that possible. It helps automate everything from EC2 and S3 to VPCs, IAM roles, and more. In this guide, we’ll walk through what the AWS provider is, how to set it up, and some best practices to follow.
What is a Terraform Provider in Terraform on AWS?
Wide array of organizations heavily utilize Terraform for its ability to support diverse infrastructure needs distributed over different cloud providers. A Terraform Provider is a plugin that serves as Terraform’s interface for managing their external APIs. Depending on your needs, you can pick from official providers like AWS, Azure, and GCP. You can pick providers from third parties and the community. These include platforms like Kubernetes, Oracle, and Alibaba. You can also choose ControlMonkey and others. This flexibility lets you tailor your infrastructure solutions across different technologies and environments.
Terraform uses plug-in-based architecture to work with hundreds of such infrastructure platforms. Terraform providers are distributed by HashiCorp and its publicly available on Terraform registry or OpenTofu Registry. There are 3 tiers of providers.
- Official Provider: Owned and maintained by HashiCorp and includes major cloud providers AWS, Azure, and GCP.
- Partner Provider: Owned and maintained by a 3rd party technology company that has gone through a partner provider process. e.g. Heroku, Digital Ocen, etc.
- Community Providers: Published and maintained by individual contributors of the community.
Terraform AWS Provider: Overview & Key Features
The Terraform AWS Provider plugin specifically enables interaction with AWS resources. It connects Terraform to the AWS Cloud. This lets you define AWS infrastructure, like EC2 instances, S3 buckets, or VPCs, in your Terraform files.
Using Terraform on AWS: Setup Guide
Terraform AWS provider is central to provisioning and managing cloud resources in an automated way. As a Terraform admin, you will go through the following steps,
Step1: Install Terraform CLI
Install Terraform CLI on your local computer.
Step 2: Initialize the Provider
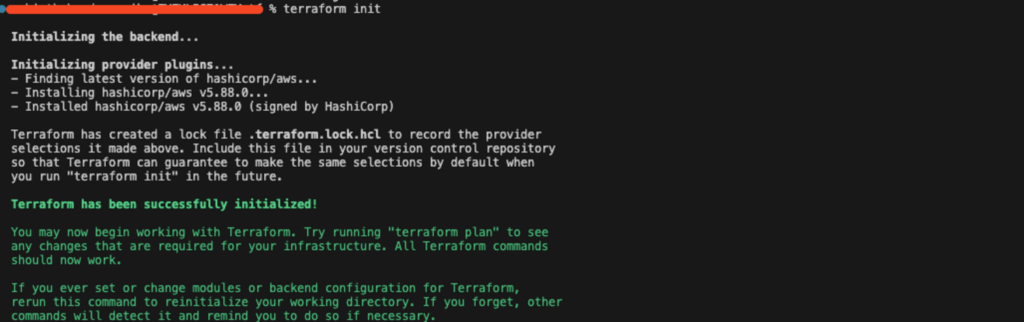
When you run terraform init, Terraform automatically downloads the AWS provider plugin.
Step 3: Define AWS Resources
In your configuration files (.tf files), specify which AWS resources you want to create.
Step 4: Validate, Plan, Apply
Use terraform validate, terraform plan, and terraform apply to review and deploy your changes. Terraform communicates with AWS APIs via the provider to create or update infrastructure.
How to Set Up Terraform AWS Provider
- Step 1: Download the latest version of Terraform from terraform.io and add it to your system path.
- Step 2: Download and configure AWS CLI. Enter the below command, and give the access key, secret access key, region, and output format in JSON.

- Step 3: aws configure – Create a Terraform configuration file
Create a file named main.tf with the AWS provider block.
|
1 2 3 4 5 6 7 8 9 10 |
# Configure the AWS Provider provider "aws" { region = "us-east-1" } resource "aws_vpc" "demo_vpc" { cidr_block = "10.0.0.0/16" tags = { name = "demo_vpc" } } |
Step 4: Initialize and Deploy – Run the “terraform init” command for initializing your backend. After that, you can run the plan for infrastructure changes, and finally apply them to AWS.
- terraform init
- terrafor plan
- terraform apply
💡 Quick Recap
- Providers connect Terraform to external APIs (AWS, Azure, etc.)
- AWS Provider is most commonly used in production environments
- You should pin your provider version and use remote state for safety
Terraform AWS provider Features and Benefits
Provider block helps set up and manage authentication access from the provider plugin to the service provider. Below is a basic example of a provider block for Terraform provider specifying the cloud region. The block configures Terraform to use AWS and create resources in the region specified. For authentication, Terraform will use credentials from your AWS CLI. It can also use environment variables like AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY, or IAM roles.
|
1 2 3 |
provider "aws" { region = "us-east-1" # Set your AWS region } |
Resource Management:
With the AWS Provider, it’s easy to specify AWS resources in a few lines of code. Whether you need an EC2 instance, an S3 bucket, or a VPC, you can define everything in a declarative style. This approach makes your infrastructure easy to version, share, and reuse.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
# main.tf provider "aws" { region = "us-east-1" } # Create a VPC resource "aws_vpc" "demo_vpc" { cidr_block = "10.0.0.0/16" tags = { Name = "demo-vpc" } } # Create a Subnet resource "aws_subnet" "demo_subnet" { vpc_id = aws_vpc.demo_vpc.id cidr_block = "10.0.1.0/24" tags = { Name = "demo-subnet" } } <strong># Create an EC2 Instance </strong> resource "aws_instance" "demo_instance" { ami = "ami-0c55b159cbfafe1f0" instance_type = "t2.micro" subnet_id = aws_subnet.demo_subnet.id tags = { Name = "demo-instance" } } |
State Management for Terraform
The AWS Provider works seamlessly with Terraform’s state management. You can store your Terraform state in AWS S3. Use DynamoDB for state locking. This stops changes from happening at the same time. It also helps avoid configuration drift. Also note that there are other backend options available, with the default being the local (Read More).
Example Configuration:
|
1 2 3 4 5 6 7 8 9 10 |
<em># backend.tf terraform { backend "s3" { bucket = "terraform-state-bucket" # Pre-existing S3 bucket key = "prod/terraform.tfstate" # State file path region = "us-east-1" # Same as provider region dynamodb_table = "terraform-locks" # Pre-existing DynamoDB table encrypt = true # Encrypt state } }</em> |
Modular Deployments
Terraform configurations can be organized into modules. When combined with the AWS Provider, you can tackle large-scale deployments by breaking infrastructure definitions into reusable, maintainable modules.
# Configure the AWS Provider (inherited from root module)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
resource "aws_vpc" "demo-vpc" { cidr_block = var.cidr_block tags = { Name = var.name } } resource "aws_subnet" "public" { vpc_id = aws_vpc.demo-vpc.id cidr_block = cidrsubnet(var.cidr_block, 8, 1) # Creates subnet from VPC CIDR tags = { Name = "${var.name}-subnet" } } |
Environment Variables in Terraform AWS Setup
Export AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, and AWS_REGION in your terminal.
|
1 2 3 4 5 6 7 |
# main.tf (no credentials in code) provider "aws" { region = "us-east-1" # Optional if AWS_REGION is set } |
Using Shared Credentials with Terraform AWS Provider
Terraform can automatically read from the default AWS CLI credentials file (~/.aws/credentials and ~/.aws/config).
|
1 2 3 4 5 6 |
provider "aws" { region = "us-east-1" shared_credentials_files = ["~/.aws/credentials"] # Default path profile = "dev-profile" # Non-default profile } |
Terraform AWS Provider Security Best Practices
Don’t hardcode credentials
Never put AWS access keys or secrets in Terraform files. Alternatively, use environment variables or shared credentials files.
- # Use environment variables (no hardcoded secrets)
- provider “aws” {region = “us-east-1” }
Encrypt state files:
When you store Terraform state in an S3 bucket, enable server-side encryption (SSE) and use KMS if possible. Also configure DynamoDB for state locking to prevent concurrent modifications.
|
1 2 3 4 5 6 7 8 9 10 11 |
#backend.tf terraform { backend "s3" { bucket = "terraform-state-bucket" key = "prod/terraform.tfstate" region = "us-east-1" dynamodb_table = "terraform-locks" encrypt = true kms_key_id = "alias/terraform-state-key" } } |
Use sensitive variables
Prevent Terraform from recording sensitive values in plain text.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
variable "aws_access_key" { type = string sensitive = true # Hides value in outputs } variable "aws_secret_key" { type = string sensitive = true # Hides value in outputs } provider "aws" { access_key = var.aws_access_key secret_key = var.aws_secret_key region = "us-east-1" } |
Conclusion
The Terraform AWS Provider is a key tool for managing cloud infrastructure. It helps you easily automate your AWS infrastructure setup and management. It works well with AWS services. You can create a safe and easy-to-manage infrastructure by using best practices. These include remote state management, IAM role-based authentication, and modular configurations.

FAQ: Terraform on AWS & More
Terraform AWS Provider can be authenticated using environment variables, shared credentials files, IAM roles, and AWS CLI profiles.
Yes, you can have multiple accounts configured using different provider aliases in Terraform.
Terraform uses state files to track resource changes. It is best to store state files remotely. For example, use AWS S3 with state locking in DynamoDB. This helps prevent conflicts in a team setting.
Terraform modules promote reusability, maintainability, and consistency in infrastructure code, allowing teams to manage complex deployments better.
You can use Terraform with CI/CD tools like GitHub Actions, Jenkins, and AWS CodePipeline. This helps you set up and change infrastructure automatically.
To update the provider, modify the provider version within your Terraform configuration and run terraform init -upgrade. Terraform AWS Provider automates infrastructure management by providing scalability, security, and automation. It can easily integrate with AWS services to offer smooth deployment and management of cloud infrastructure. With Terraform AWS Provider, organizations can achieve consistency, reduce manual intervention, and maximize cloud governance.
Run terraform providers in your project directory. It lists all providers and their versions. To specify or check the required version in your config, use:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
}
You can also run terraform init -upgrade to refresh to the latest version that matches constraints.
This usually happens due to one of the following:
- Network issues or firewall blocking Terraform’s access to the registry
- misconfigurations of the Proxy
- DNS problem
- Using an outdated Terraform version that doesn’t support the current provider structure
Fixes:
- Check internet access and firewall rules
- Try running terraform init -upgrade with a clean .terraform directory
- Update to the latest Terraform CLI
- Try using the TF_LOG=DEBUG environment variable to troubleshoot further