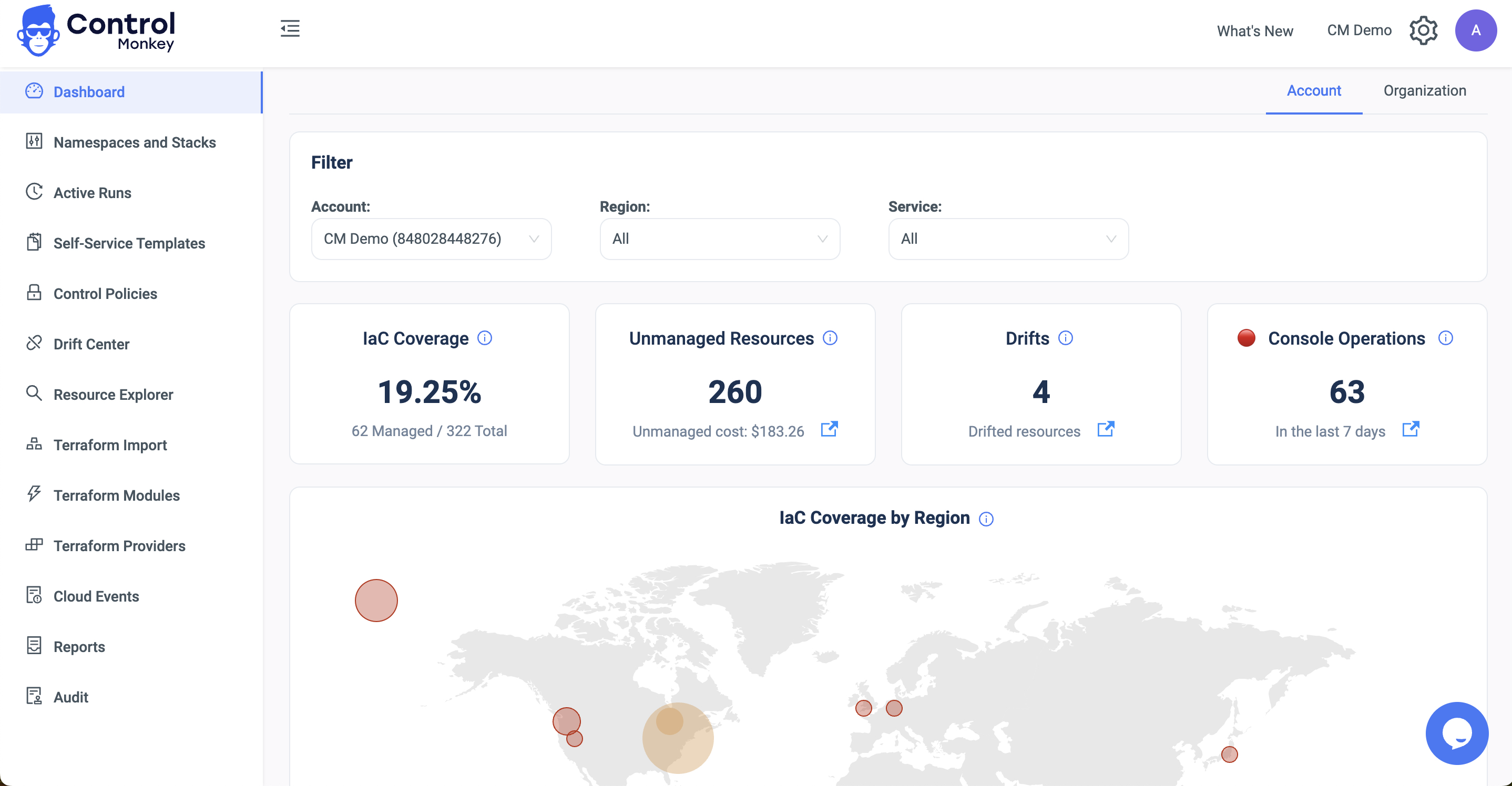
Managing cloud costs effectively is a top priority for businesses using AWS. Without proper governance, infrastructure sprawl and misconfigurations can lead to unexpected expenses. This is where AWS CloudFormation comes in. It is a strong Infrastructure as Code (IaC) service. It helps with cost optimization, especially when used with cloud cost optimization tools. These tools improve visibility and control over resource use.
AWS CloudFormation allows you to define and manage cloud resources using declarative templates, ensuring consistent deployments while automating resource provisioning. When integrated with cloud cost optimization tools and AWS cost optimization tools, CloudFormation helps organizations identify and eliminate wasteful spending.
- Prevent over-provisioning by automating the creation and deletion of resources.
- Maintain version-controlled infrastructure, improving visibility and cost tracking.
- Utilize CloudFormation hooks to monitor and predict costs before provisioning.
- Enforce cost-efficient infrastructure setups with pre-defined templates for teams.
By leveraging these capabilities, organizations can streamline operations, prevent cost overruns, and ensure long-term cloud cost efficiency. In this article, we’ll explore how to use CloudFormation to reduce your AWS bill without compromising performance or scalability.

1. Automate AWS Resource Lifecycle for Cost Optimization
Over-provisioning leads to unnecessary AWS costs. CloudFormation automates resource creation and deletion, ensuring only necessary infrastructure runs.
Automate Resource Lifecycle Using CloudFormation Stacks
CloudFormation stacks streamline deployment and removal of resources:
- Temporary environments: Create dev/test environments that auto-delete after use.
- Stack deletion: Ensure unused resources are fully removed.
Use Stack Policies to Avoid Costly AWS Mistakes
- Restrict scaling: Prevent accidental Auto Scaling increases.
- Protect key resources: Block deletion of essential S3 buckets or RDS instances.
Automate Cost Cleanup with Scheduled Stack Deletions
- EventBridge + Lambda: Auto-delete non-prod stacks after hours.
- Expiration policies: Remove test environments after a set period.
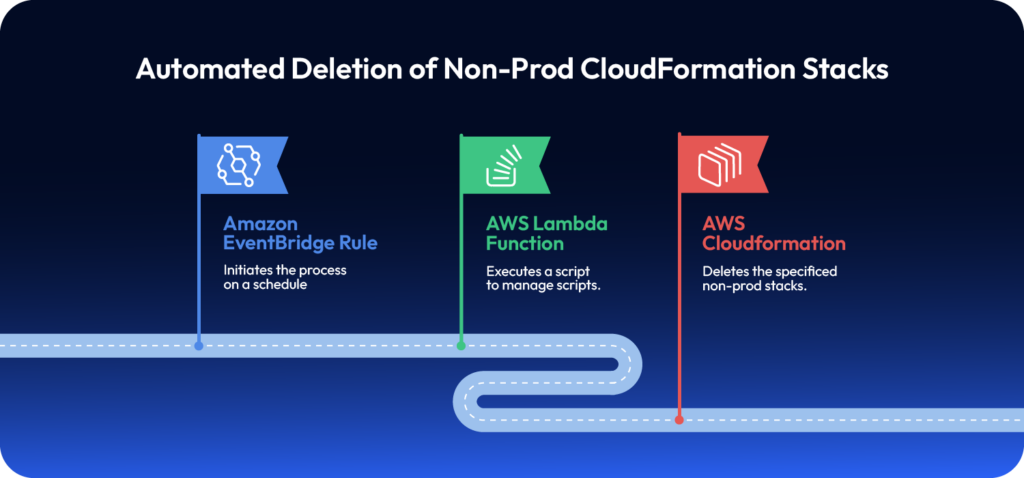
Example: Auto-Cleanup Dev Environment
A team provisions EC2, RDS, and S3 via CloudFormation. A scheduled EventBridge rule deletes the stack every Friday at 6 PM, preventing weekend waste.
2. Improve AWS Cost Transparency with Version Control
Untracked infrastructure changes can lead to unexpected cost increases. AWS CloudFormation, when integrated with version control and change management, ensures infrastructure modifications are auditable, controlled, and cost-efficient.
Use Git for CloudFormation Cost Optimization Tracking
CloudFormation templates should be stored in Git repositories (GitHub, GitLab, AWS CodeCommit) to enable:
- Change tracking: Every modification is version-controlled, preventing unapproved resource deployments.
- Rollback capability: If a change leads to cost spikes, revert to a previous template version.
- Code reviews: Teams can enforce peer reviews before applying infrastructure changes.
Example Git Workflow for CloudFormation:
- Developers create/update a CloudFormation template (infrastructure.yaml).
- The change goes through a pull request (PR) for review.
- A CI/CD pipeline validates the template using AWS CloudFormation Linter (cfn-lint).
- After approval, the stack is updated using AWS CloudFormation StackSets.
Detect Costly AWS Infrastructure Drift
AWS CloudFormation Drift Detection ensures deployed resources match the expected configuration. Undocumented changes can result in higher costs.
Steps to detect drift:
- Run aws cloudformation detect-stack-drift –stack-name MyStack.
- Check drift results with aws cloudformation describe-stack-drift-detection-status.
- If unexpected cost-impacting changes (e.g., increased instance sizes) are detected, restore the stack to its last known good state.
Enforce Cost Controls with AWS Budgets and Change Sets
AWS Budgets: Set budget alerts to detect cost anomalies before CloudFormation updates exceed thresholds.
- Change Sets: Before applying a stack update, use:
aws cloudformation create-change-set –stack-name MyStack –template-body file://infrastructure.yaml
This allows teams to preview changes, avoiding unintended cost increases.
Example: Preventing Costly Resource Scaling
A team updates an Auto Scaling Group in CloudFormation. Before applying, they:
- Use cfn-lint to validate the template.
- Generate a change set to preview new instance counts.
- Compare with AWS Budgets; if costs exceed limits, they reject the update.
3. Use AWS CloudFormation Hooks with Cost Optimization Tools
AWS CloudFormation Hooks allow proactive cost management by enforcing policies before deploying infrastructure. Hooks validate resources during stack creation and updates, preventing misconfigurations that could lead to cost overruns.
How CloudFormation Hooks Support Cost Optimization
CloudFormation Hooks are triggered before a stack operation is executed. They use AWS Lambda functions to validate and enforce cost-related policies.
- Pre-create validation: Ensure only cost-optimized resources are deployed.
- Pre-update checks: Block expensive modifications (e.g., oversized EC2 instances).
- Policy enforcement: Restrict deployments that exceed cost thresholds.
Example: Enforcing Cost Limits on EC2 Instances
A CloudFormation Hook can prevent expensive EC2 instance types from being deployed.
-
Create a Lambda function for the hook
This function inspects the CloudFormation request and rejects costly instances.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
import json def lambda_handler(event, context): allowed_instances = ["t3.micro", "t3.small", "t3.medium"] for resource in event["requestData"]["resourceProperties"]: if resource["Type"] == "AWS::EC2::Instance": instance_type = resource["Properties"]["InstanceType"] if instance_type not in allowed_instances: return {"status": "FAILED", "message": f"Instance type {instance_type} exceeds cost policy"} return {"status": "SUCCESS"} |
-
Register the hook with AWS CloudFormation
|
1 2 3 4 |
aws cloudformation register-type \ --type HOOK \ --type-name CostOptimizationHook \ --schema-handler-package s3://my-bucket/hook-package.zip |
Predict AWS Costs Using Cloud Cost Optimization Tools
Hooks can also be integrated with AWS Cost Explorer to predict expenses before deployment.
- Check estimated costs: Query AWS Cost Explorer API within a hook to estimate resource pricing.
- Deny deployments over budget: If projected costs exceed a threshold, the hook blocks deployment.
Example: Predicting EC2 Costs Before Deployment
A hook calls AWS Cost Explorer to fetch the projected monthly cost of an EC2 instance and prevents deployment if it exceeds a predefined budget.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
import boto3 cost_client = boto3.client("ce") def get_estimated_cost(instance_type): response = cost_client.get_cost_and_usage( TimePeriod={"Start": "2023-01-01", "End": "2023-01-31"}, Granularity="MONTHLY", Metrics=["BlendedCost"], Filter={"Dimensions": {"Key": "INSTANCE_TYPE", "Values": [instance_type]}} ) return float(response["ResultsByTime"][0]["Total"]["BlendedCost"]["Amount"]) def lambda_handler(event, context): budget_limit = 50.0 # Set monthly budget per instance for resource in event["requestData"]["resourceProperties"]: if resource["Type"] == "AWS::EC2::Instance": instance_type = resource["Properties"]["InstanceType"] estimated_cost = get_estimated_cost(instance_type) if estimated_cost > budget_limit: return {"status": "FAILED", "message": f"Estimated cost of {instance_type} exceeds budget"} return {"status": "SUCCESS"} |
4. Deploy Cost-Optimized Infrastructure with CloudFormation Templates
Pre-defined CloudFormation templates ensure teams deploy cost-optimized infrastructure while maintaining compliance with best practices. By standardizing configurations, organizations reduce unnecessary spending, enforce governance, and prevent misconfigurations.
Cost Benefits of Using AWS Pre-Defined Templates
- Enforce cost-efficient resource selection (e.g., restrict to low-cost EC2 instances).
- Enable self-service deployments without cost risks.
- Ensure consistency across environments (dev, test, prod).
CloudFormation Example: AWS Cost Optimization Template
A standardized CloudFormation template ensures developers use only approved, cost-efficient instance types and storage options.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
AWSTemplateFormatVersion: "2010-09-09" Description: "Pre-defined cost-optimized infrastructure template" Resources: MyEC2Instance: Type: AWS::EC2::Instance Properties: InstanceType: t3.micro # Restrict to a cost-effective instance ImageId: ami-0abcdef1234567890 Monitoring: false # Disable detailed monitoring to reduce CloudWatch costs MyRDSInstance: Type: AWS::RDS::DBInstance Properties: Engine: "mysql" DBInstanceClass: "db.t3.micro" # Use a budget-friendly RDS instance AllocatedStorage: 20 # Avoid unnecessary storage over-allocation StorageType: "gp2" MultiAZ: false # Disable Multi-AZ for non-production workloads |
Enforce Cost Governance Using AWS Optimization Tools
AWS Service Catalog allows organizations to pre-approve CloudFormation templates, ensuring teams only deploy cost-optimized resources.
Steps to implement:
- Define cost-efficient infrastructure templates.
- Store them in AWS Service Catalog as product portfolios.
- Grant teams self-service access while restricting unauthorized modifications.
Enforce AWS Cost Policies via CloudFormation StackSets
CloudFormation StackSets enforce cost-efficient infrastructure across multiple AWS accounts. For example, an organization can:
- Enforce tagging policies to track costs (Environment: Production).
- Restrict large instance types globally.
- Automatically apply scaling limits across environments.
|
1 2 3 4 |
aws cloudformation create-stack-set \ --stack-set-name CostOptimizedInfrastructure \ --template-body file://cost_optimized_template.yaml \ --capabilities CAPABILITY_IAM |
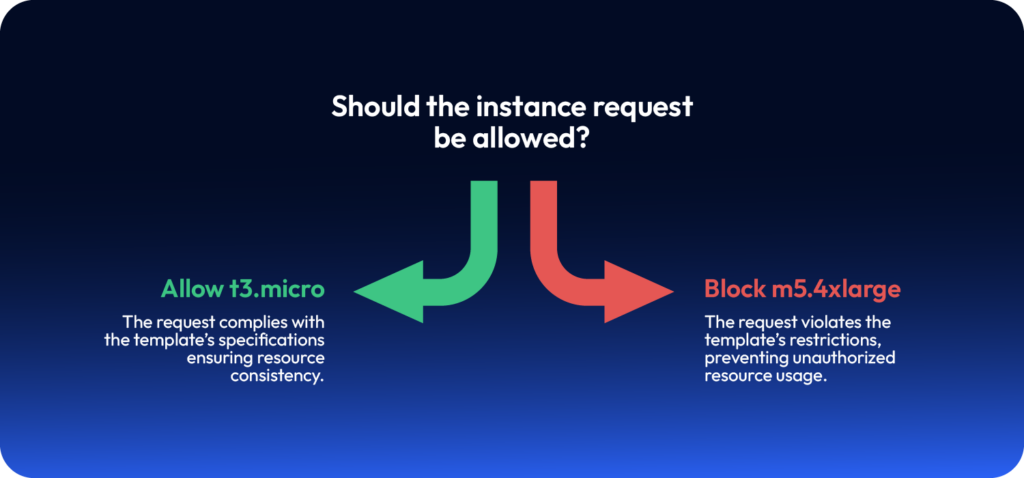
Example: Preventing Costly Deployments
A developer tries to launch an m5.4xlarge instance, but the pre-defined template only allows t3.micro, enforcing cost control automatically.
Final: AWS CloudFormation and Costs Optimization
AWS CloudFormation is a powerful tool for cost optimization in cloud environments. Organizations can reduce unnecessary expenses, maintain governance, and ensure predictable cloud spending by automating resource lifecycle management, enforcing version control, utilizing CloudFormation Hooks for cost tracking, and leveraging pre-defined templates.
By adopting these best practices:
- Prevent over-provisioning through automated resource creation and deletion.
- Enable cost transparency with version-controlled infrastructure.
- Track and predict costs using CloudFormation Hooks.
- Standardize deployments with cost-efficient templates and Service Catalog.
Implementing these strategies ensures that cloud infrastructure remains efficient, scalable, and cost-effective—helping businesses optimize their AWS bill without compromising performance or security.
With ControlMonkey, you can optimize CloudFormation usage at scale – automate stack lifecycles, detect cost drifts in real time, and enforce budget-friendly templates across environments. Gain full visibility into your infrastructure spend, prevent over-provisioning, and deploy smarter with built-in guardrails for cost efficiency. Eliminate cloud waste before it happens.