As a DevOps professional, you’ve likely spent weeks carefully designing and documenting your infrastructure to ensure everything runs smoothly. But over time, unexpected issues and vulnerabilities begin to surface. These aren’t just bugs—they’re symptoms of inconsistent cloud governance, especially common in fast-scaling DevOps environments. Without adopting cloud governance best practices, your once-reliable applications start to fail, and your team scrambles to understand why. Sound familiar? Welcome to the world of configuration drift.
So, have you wondered why this is happening over and over again and how can we fix it? In reality, developers make quick fixes, administrators apply patches, and before you know it, your perfectly documented configurations are out of date. When under pressure, we naturally cut corners and make small changes without documenting them. We often think, “I’ll document it later,” but rarely do so. Over time, these inconsistencies snowball into a disconnected, unreliable infrastructure.
In this article, we’ll explore five proven cloud governance best practices to help prevent configuration drift and maintain infrastructure integrity:
5 Proven Best Practices
- Implement Infrastructure as Code (IaC)
- Continuously detect configuration drift
- Gain full infrastructure visibility
- Automate remediation with intelligence
- Conduct audits and code reviews
Cloud Governance Best Practice #1: Use Infrastructure as Code (IaC)
Without IaC, you would first provision your infrastructure and then document it. Maintaining the scripts, documentation, and instructions you used to set up your environment is time-consuming. With IaC, you use a tool such as Terraform, AWS CloudFormation, or Ansible to maintain infrastructure as code declaratively. This makes collaboration possible.
By version-controlling your infrastructure code, you can track changes over time, automate deployments to reduce the risk of manual misconfigurations and maintain a single source of truth for infrastructure. Your IaC repository will be your “reference point” for detecting drifts in your actual infrastructure.
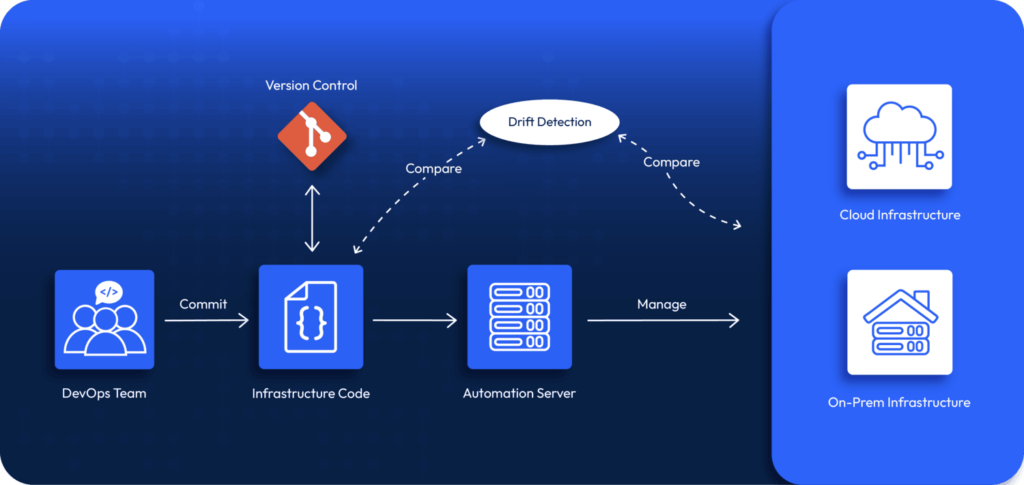
For many teams managing complex, growing cloud environments, adopting Infrastructure as Code is just the first step. In this AWS blog, you can see how ControlMonkey helps organizations apply Terraform-based cloud governance across large-scale AWS deployments.
Cloud Governance Best Practice #2: Continuously Detect and Analyze Configuration Drift
However, configuration drifts can still occur even with a well-defined IaC strategy. Someone can still make an emergency change through the cloud console, or third-party tools could apply recommended fixes to your infrastructure. Therefore drifts can happen due to all sorts of reasons, and have ramifications of different scales. Continuous drift detection is necessary to identify such changes as and when they happen.
Here are the things you should consider when selecting a drift detection solution:
- Complete visibility across all infrastructure components to ensure no blind spots where drift can hide.
- Automated detection that runs frequently enough to catch drifts as they happen.
- Actionable notifications that provide context about what changed and potential impact, not just alerts that something happened.
- Classification of drifts to identify between acceptable drift (like auto-scaling) and unauthorized or manual changes.
- Change history to track patterns over time and identify systemic issues rather than individual occurrences.
- Remediation that resolves drift both ways: cloud to code, and code to cloud
For drift detection, you can use tools like driftctl or run the ‘Terraform Plan’ command periodically. You can also integrate these tools into a CI/CD pipeline that runs periodic checks and sends timely notifications. If your multi-cloud infrastructure requires advanced drift analysis features, specialized solutions such as ControlMonkey’s Drift Detection can save time for teams that want to optimize their processes for drift management and remediation at scale.
Try to choose a tool that aligns with the criticality of applications you run on your infrastructure.
By proactively applying cloud governance best practices, DevOps teams can avoid configuration drift before it affects production systems.
Tip: Read our full guide for drift detection: https://controlmonkey.io/blog/the-definitive-guide-for-terraform-drift-detection/
Practice #3: Gain Full Visibility Across Your Cloud Infrastructure
Have a clear visibility on your entire infrastructure to identify blind spots that are not managed by IaC. Import those resources to IaC.
Cloud Governance Best Practice #4: Automate Remediation Using Intelligent Drift Analysis
Detecting configuration drift is only half the battle—you must also have a plan to remediate drift efficiently.
Automated remediation ensures that drift is corrected automatically without manual intervention. Intelligent remediation workflows can:
- Automatically rollback detected drifts to the state defined in IaC.
- Trigger alerts and approval processes for sensitive modifications (This requires classification capabilities).
- Provide detailed audit logs of detected drift and applied fixes.
Finding the cause of the change is just as important as remediating it. Some changes might be necessary, and you must incorporate them into IaC (e.g. when a third-party security tool updates security groups via AWS CLI).
By leveraging infrastructure automation tools, teams can significantly reduce mean time to resolution (MTTR) for drift-related issues, minimizing downtime and security risks.
DevOps teams can easily remediate issues in small-scale deployments by creating pipelines that periodically execute Infrastructure as Code tools against infrastructure code.
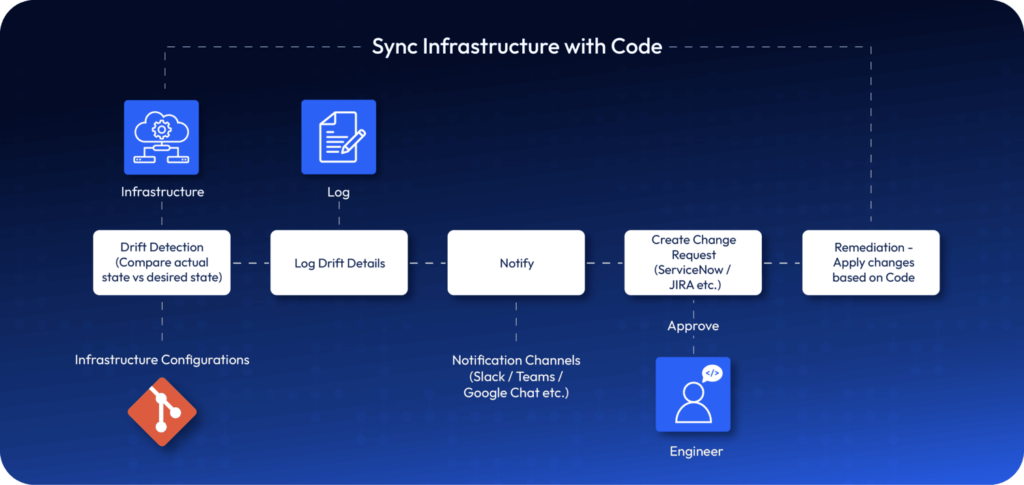
However, remediation is not limited to rolling back infrastructure but also incorporating valid changes to your code. Modern DevOps requires granular control over han
dling drifts with specialized tools for automated remediation, classification of drift items by criticality, audit logs on who and what caused the change, visual representation of changes, and automated incorporation of infrastructure changes to code.
Cloud Governance Best Practice #5: Conduct Audits, Reviews, and Foster Human Oversight
Technology solutions alone cannot stop all configuration drift. Organizations must maintain human oversight, mainly through regular audits and code reviews. We now have a growing amount of AI-generated code in our IaC repositories. Therefore, we need human-in-the-loop practices at the organizational level.
These practices aim to improve awareness and accountability. It allows teams to create infrastructure that matches business goals.
- Scheduled infrastructure reviews to regularly examine infrastructure for alignment with business needs.
- Peer code reviews to ensure IaC changes meet quality and security standards.
- Compliance audits to verify infrastructure against regulatory requirements.
- Sessions for teams on change management and standard processes.
Final Thoughts on Cloud Governance Best Practice
These cloud governance best practices provide a scalable approach to managing modern infrastructure complexity and eliminating silent failures caused by configuration drift.
Configuration drift is a challenge that increases proportionally with infrastructure complexity. As infrastructure grows, making sure that it is configured as intended and complies with standards becomes a challenge. Infrastructure-as-code (IaC) and Policy-as-code (PaC) are the minimum for consistent and manageable infrastructure.
IaC and PaC are the reference points for what the infrastructure should be.
The key to managing configuration drift is combining automation with the right tools and intelligence. ControlMonkey offers an advanced solution to detect, track, and automatically remediate configuration drift, helping organizations to maintain infrastructure integrity and compliance.
Explore how ControlMonkey enables resilient cloud governance—book a demo today.