Less than a decade ago, most teams ran dev, staging, and production in a single cloud account. Today, that seems unimaginable. Now, you start your cloud journey with at least 10 AWS accounts. One for each environment: one for networking; one for logging; one for security; one for… you get the idea.. And if you have multiple business units or products? Multiply all that by at least three. None of this is wrong, per se. It’s how AWS, Azure, and GCP tell us to do it. But that doesn’t mean it’s easy… or sustainable. When we started ControlMonkey, I spun up infra, of course. A week later, one of our developers asked: “Why do we already have so many cloud accounts?” He was joking, kind of.
Because the number of accounts isn’t the real problem. The real problem is how cloud leaders manage them.
TL;DR – multi-account cloud complexity
Cloud sprawl is inevitable – but complexity isn’t. The real problem isn’t too many accounts; it’s too little visibility, automation, and resilience. IaC isn’t enough unless every change goes through it. Control comes from how you govern, not how much you scale.
[This post was originally published in Dzone]
The Problem Isn’t Multi-Account Cloud. It’s Multi-Everything.
Once you’re operating across dozens of cloud accounts, here’s what gets harder, almost instantly:
- Visibility: You’re jumping between tabs, dashboards, and logs just to find what’s running where.
- Security & compliance: Every account becomes another attack surface. Another audit trail. Another backlog.
- Knowledge retention: The engineer who set up that “legacy” account is gone—and so is the context.
- Engineering Toil: Manual tickets. Console clickops. Drift investigations. Everyone’s firefighting.
And this isn’t just about clouds. Throw in SaaS tools, observability platforms, CI/CD systems, and version control, too. Now, you’re managing dozens of systems that impact your infra footprint.
The future of all this is clear: there will be more accounts, infra and requirements, with less institutional knowledge than today as team members leave, and no slowdown in delivery expectations.
If your operating model can’t keep up, all this complexity is a recipe for chaos.
Everyone Knows the Answer: Infrastructure as Code
First, let’s be honest—just having Terraform or OpenTofu doesn’t mean you’re using it at scale, consistently, or safely. Iac by itself coverage isn’t a panacea.
I suggest asking yourself (because I ask myself):
- Are all infra changes going through code?
- Can anyone bypass the pipeline with a manual change?
- Are you constantly triaging alerts and rolling things back?
In my experience, most cloud teams don’t need to be convinced IaC is the answer. The real problem is enforcement and scale. Unless you can guarantee every change goes through code, you’re flying blind, and paying for it in accumulating tickets, toil, and risk.
Wear a Seatbelt…And Drive Faster.
Here’s how I think about it (with another transportation metaphor)
Cloud teams today are driving 100 mph in a dense fog. We’re accelerating delivery, shipping faster, deploying AI workloads, expanding globally. But without visibility and control? You’re speeding without a seatbelt.
A resilient (read: seat-belted) multi-account strategy starts with three things:
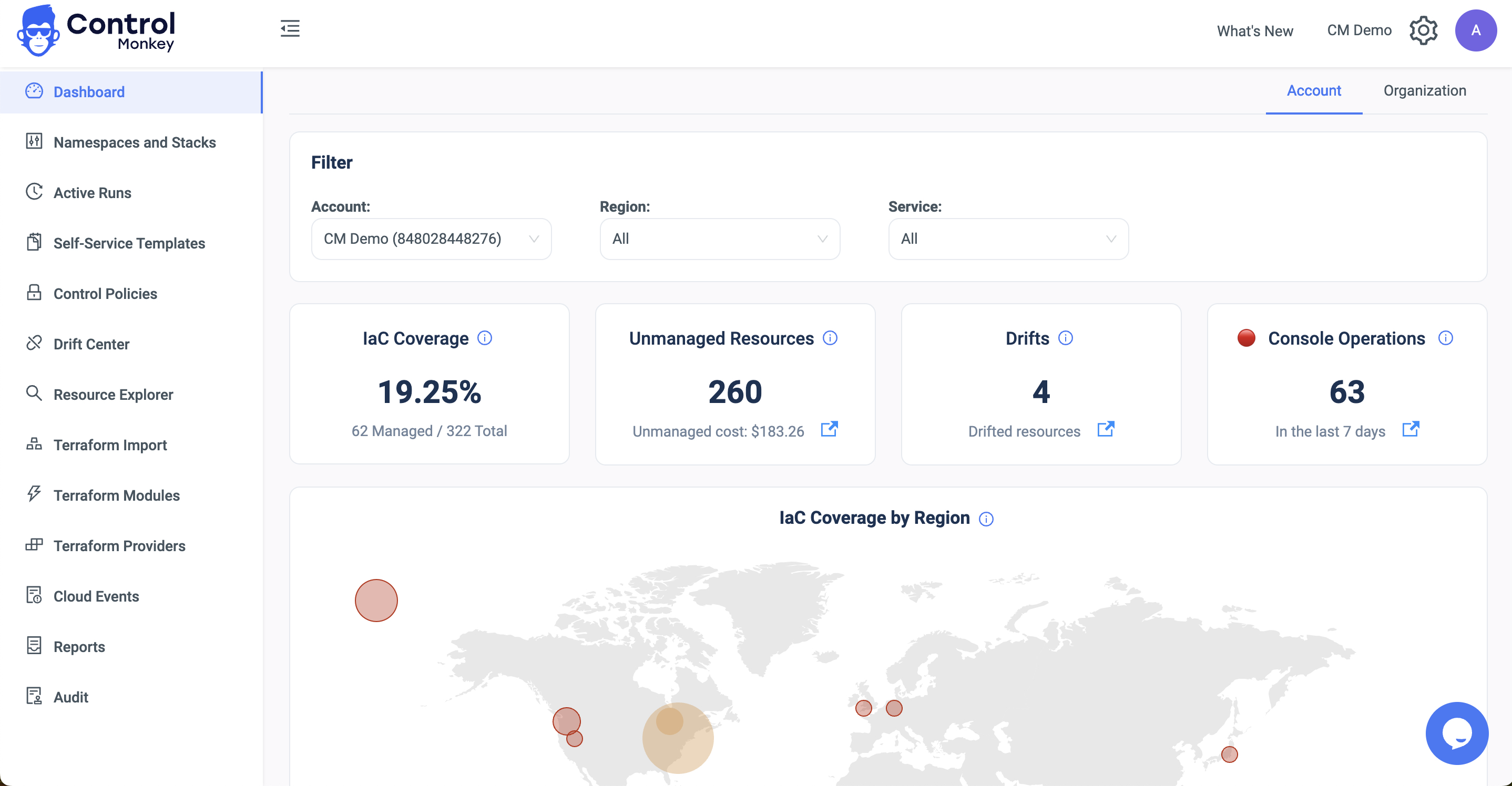
- Total Visibility: You can’t govern what you can’t see. Every account, every resource, every pipeline—visible in one place. Dashboards, not detective work.
- Total Automation: Infrastructure should only be delivered one way: through code. No manual shortcuts. No one-off pipelines. Just one path to prod, by design.
- Total Resilience: All configuration is backed-up and every change is validated and policy-aligned before it reaches production. That’s what lets your team sleep at night—and build during the day.
And if you don’t have these things? You’ll feel it every where: security issues, compliance audits, attrition and endless toil. Meanwhile, the rest of the business isn’t waiting. AI, product velocity, global expansion—these don’t pause while you figure out how to regain control.
So, what to do?
Where to Start: 5 Questions in 10 Minutes
I know from experience you don’t need a 12-month roadmap to get started. Just take 10 minutes and answer these five questions honestly:
- What’s your real IaC coverage—by environment?
- Can you detect if someone bypasses your Terraform or OpenTofu pipeline?
- How much time does your team lose to Infra PR back-and-forths and manual reviews?
- Are you going to manage more infra in the next 12–24 months?
- Can you prove your production infra is compliant right now—without manual digging?
If any of those made you pause—it’s probably already costing you.
Whether you build your own framework or adopt a platform is up to you,If it is Multi-Cloud on Opentufo or Terraform, What matters is that you stop accepting cloud sprawl as inevitable and start governing all those accounts…
Total visibility. Total automation. Total resilience. That’s how you stay in control—no matter how fast you’re going