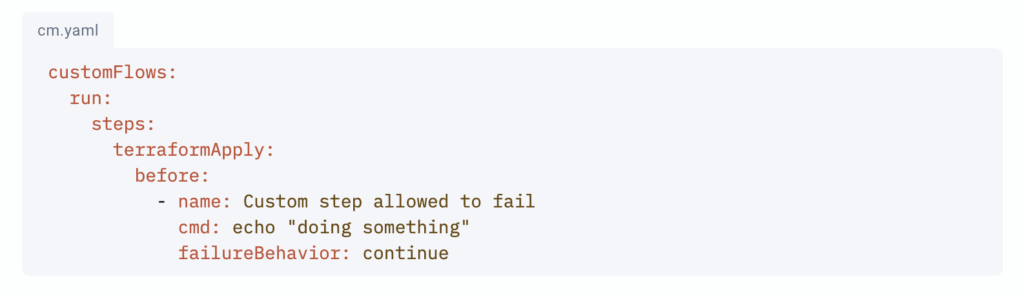
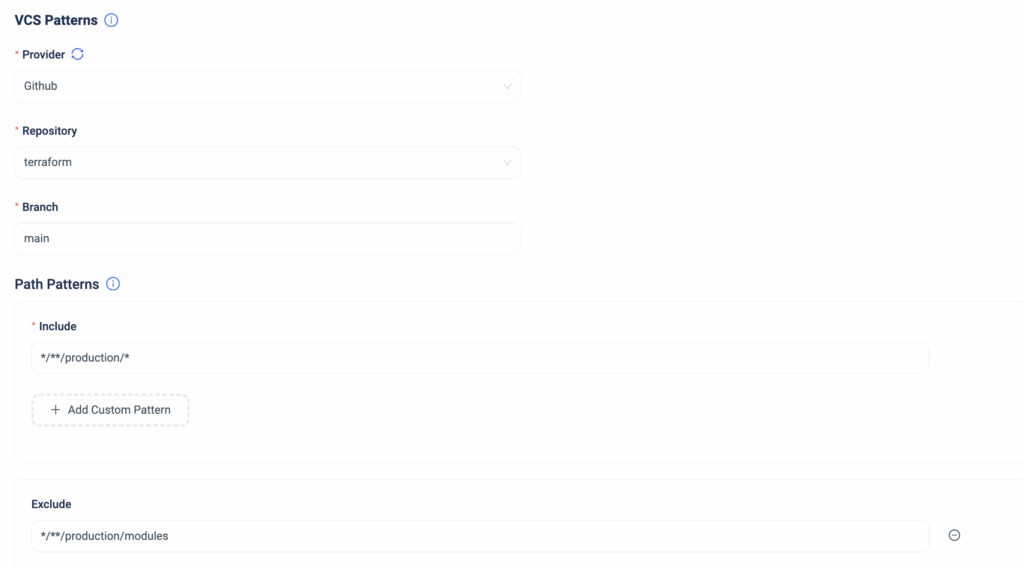
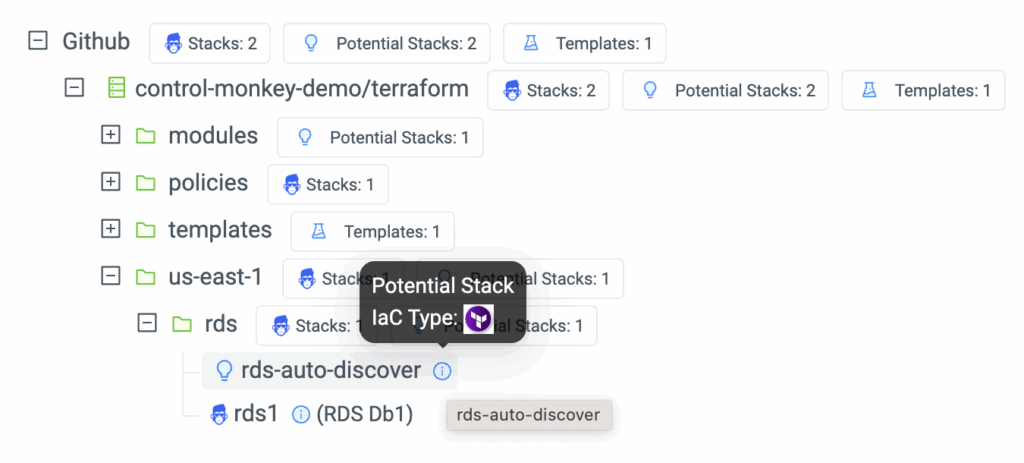
Managing cloud infrastructure at scale requires complete visibility into every change.
But what happens when someone bypasses Terraform and modifies resources directly in the GCP console?
These untracked console changes, AKA ClickOps, can lead to drifts, misconfigurations, compliance violations, and security risks. Without visibility into these actions, teams are left troubleshooting unexpected issues instead of proactively managing their cloud.
Today, we’re excited to introduce ClickOps Scanner for GCP, a new capability for Google Cloud users that tracks and detects console operations across your GCP projects, ensuring that all infrastructure changes stay accounted for.
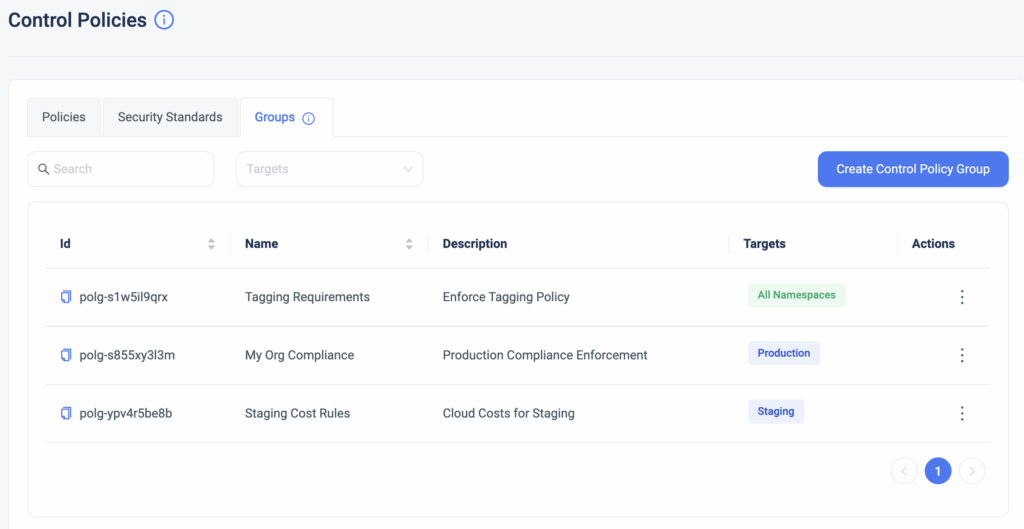
ClickOps Scanner for GCP
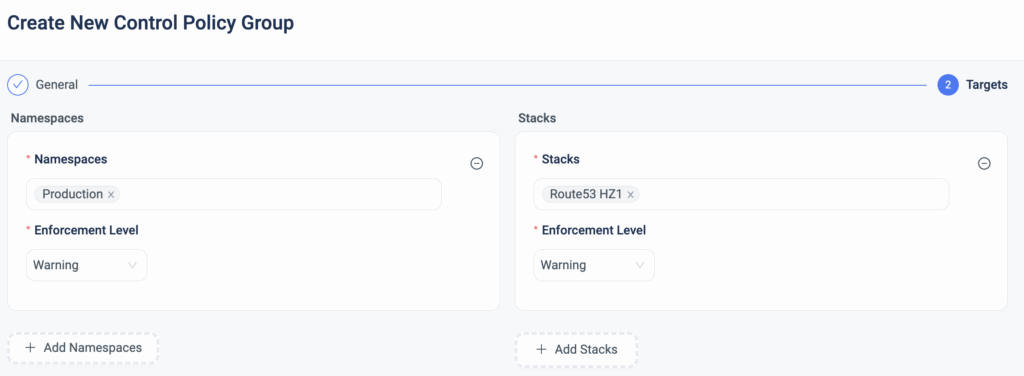
With ClickOps Scanner for GCP, ControlMonkey users can now:
- Monitor every change in real-time across GCP projects, whether intentional or unexpected.
- Resolve Terraform Drifts faster by quickly detecting the Cloud Event (ClickOps) that caused the configuration drift and shorten investigation and resolution times.
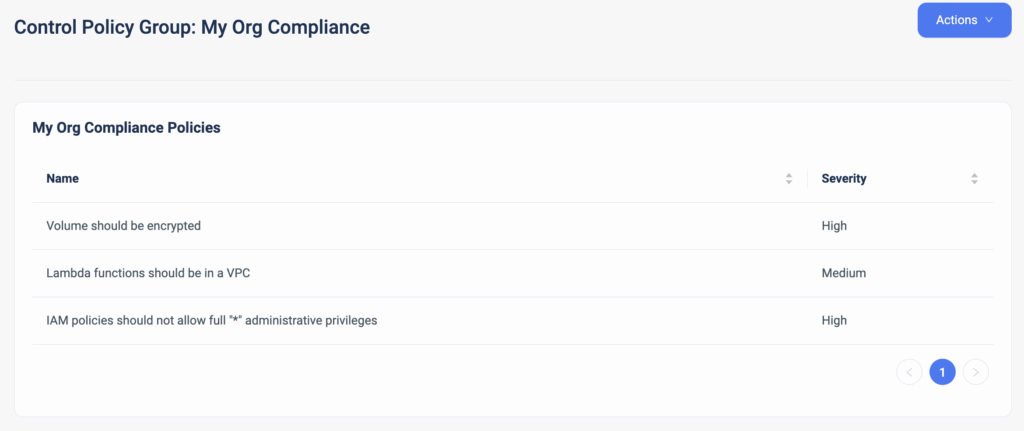
- Ensure compliance and security by keeping a complete audit trail of all infrastructure changes made through code or the console.
- Speed up debugging and root cause analysis. Quickly trace changes back to their source and understand the impact of every action.
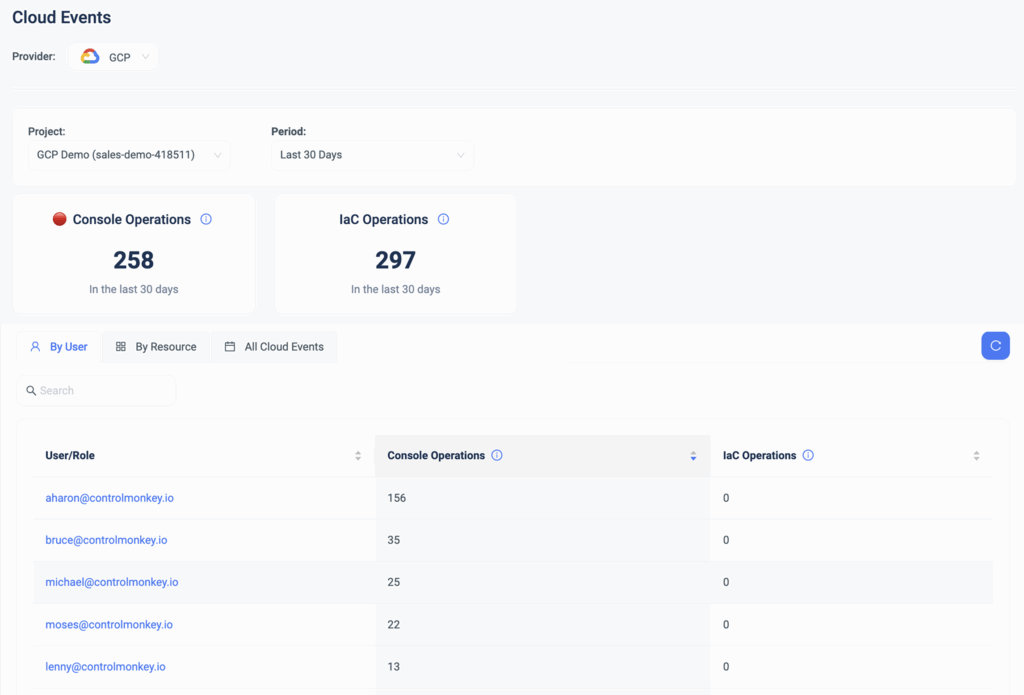
Bring Total Cloud Control to your GCP Environment
Untracked console operations can create security risks and disrupt infrastructure stability.
With ClickOps Scanner for GCP, you get a complete insight into every manual change, so nothing slips through the cracks.
Ready to take control of your infrastructure?
Meet with our Terraform experts for a 30-minute technical call to learn more.