As cloud operations scale, the skills gap – not tooling – often becomes a bottleneck. Modern DevOps teams need more than automation; they need an assistant that understands their codebase, cloud state, and guardrails and can help them with shipping infra with confidence, without sacrificing speed. Today we are lunching ControlMonkey AI IaC CoPilot to answer those challenges.
Introducing KoMo: First AI IaC Copilot
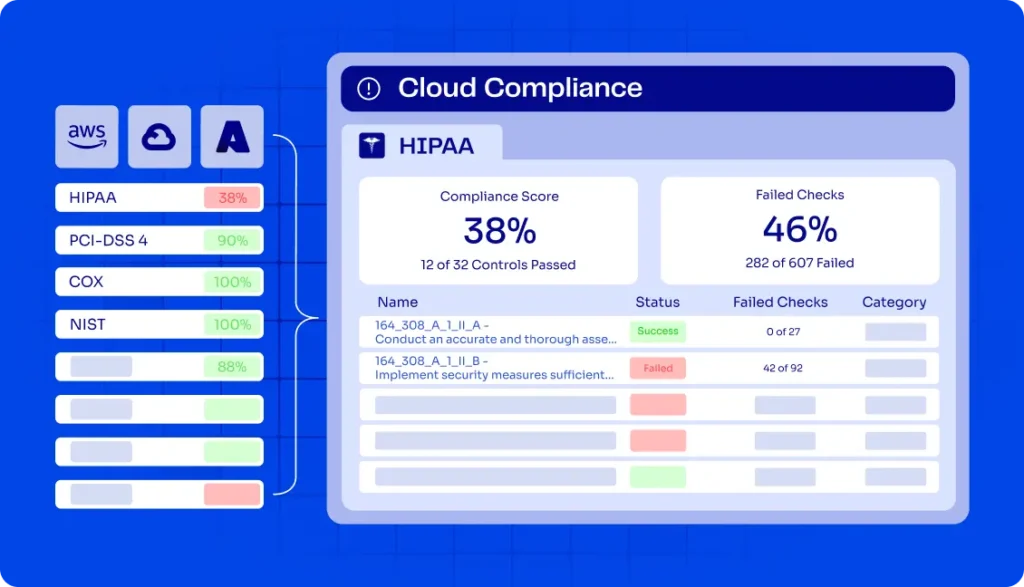
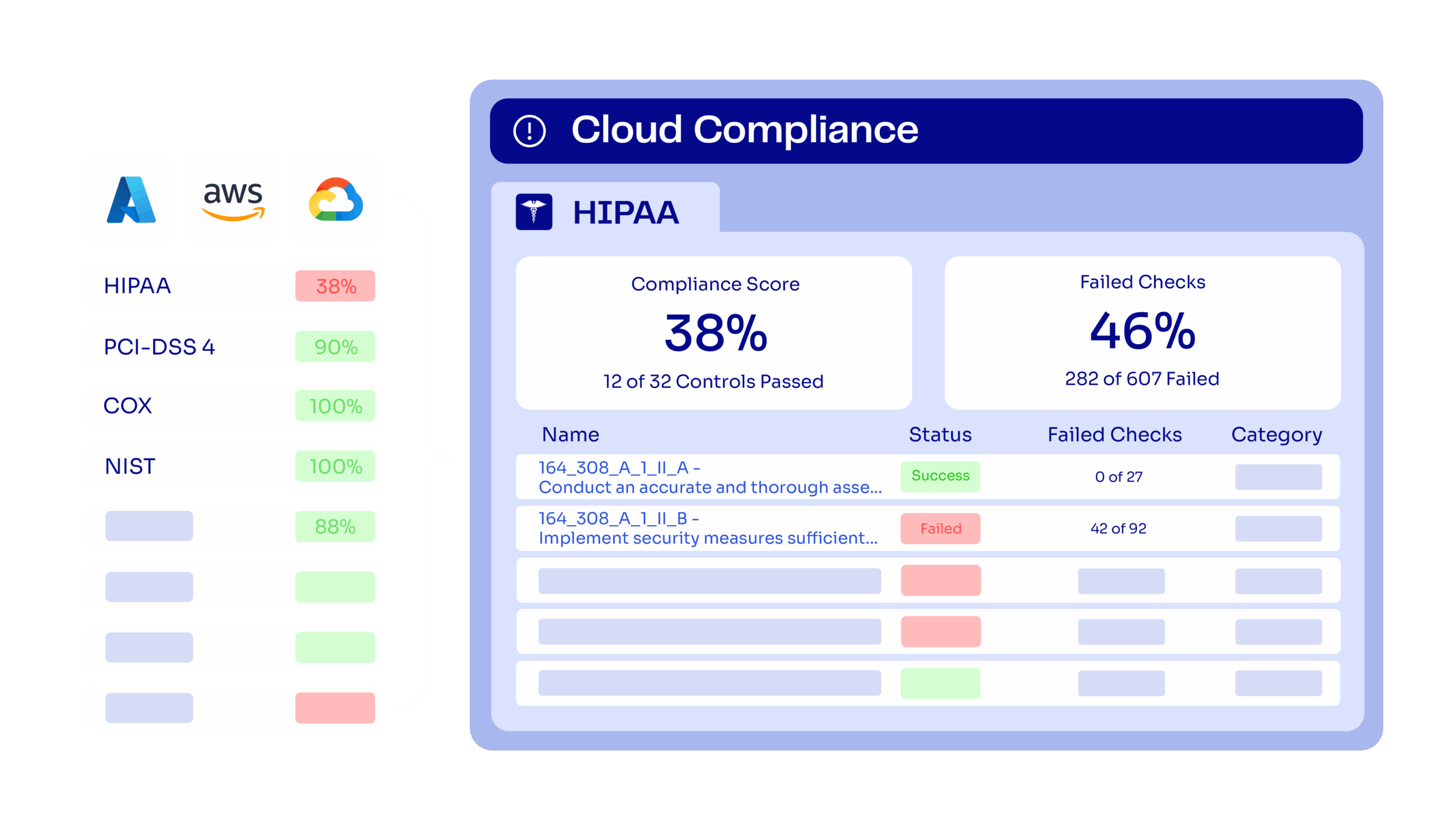
ControlMonkey, the industry’s only fully end-to-end IaC cloud automation platform, today announced KoMo, an AI-powered copilot designed to eliminate one of the biggest blockers in infrastructure delivery: the Infrastructure-as-Code (IaC) skills gap.
The Problem: The Skills Gap
Infrastructure delivery bottlenecks often trace back to one place: the skills gap. Teams can only move as fast as their least experienced engineer, slowing throughput, inflating costs, and introducing compliance risk. Senior DevOps become gatekeepers instead of innovators, while less-experienced contributors hesitate over Terraform syntax, plans, and reviews that can take a time and create toil.
KoMo: The Evolution of Self-Service
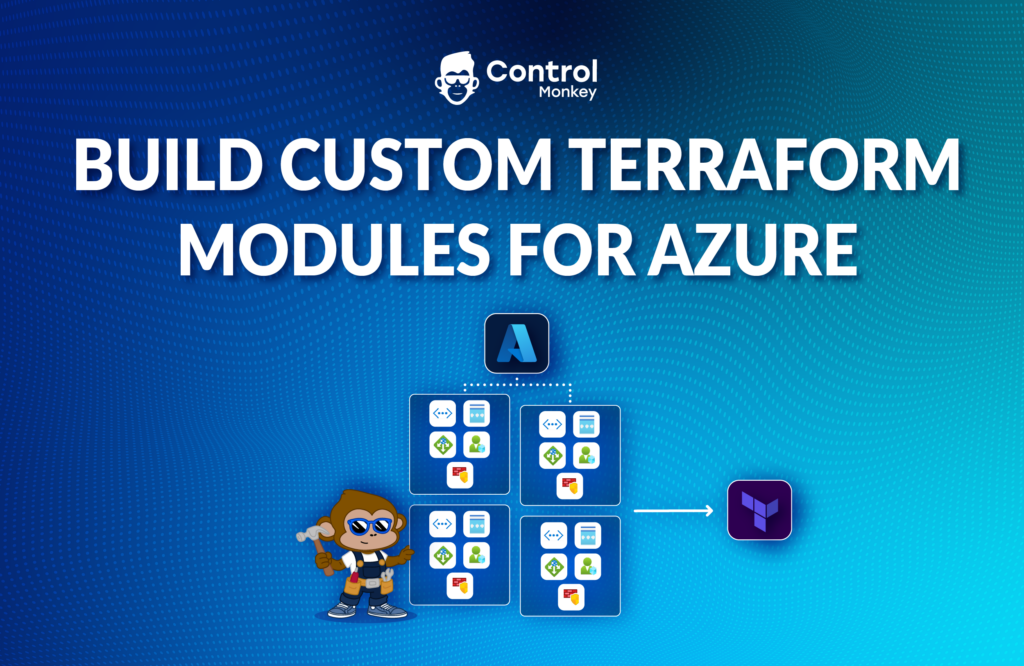
Traditional self-service relies on static blueprints. That’s fine for provisioning a single resource, but brittle when real-world requirements change. Our new AI IaC Copilot evolves self-service into something dynamic: AI-driven, context-aware, and compliant by design.
Unlike generic AI chat solutions like ChatGPT or Perplexity that are based on public knowledge KoMo operates with full organizational context thanks to Controlmonkey Integration to the Cloud accounts and to the Git.
KoMo Understand:
- Code across every IaC repository
- Cloud resources currently running in the environment
- Policies and guardrails that enforce compliance, security, and cost standards
- Deployment history, including approvals, rollbacks, and failures
- Modules and best practices shared across the organization
KoMo doesn’t generate generic Terraform. It generates Terraform code for YOUR organization – that is compliant, contextual, and safe to deploy. Engineers can request exactly what they need, and KoMo builds the stack the way your organization specifies.
KoMo: AI IaC Copilot Key Capabilities
- Generate Terraform for new resources and stacks aligned to org modules and policies
- Explain Terraform plans in clear, human-readable language
- Trace dependencies, module usage, and historical context instantly
- Flag risk before deployment in context from older outcomes.
- Enforce module usage to prevent drift and “left-behind” resources
- Cover multi-repo environments to eliminate blind spots
- Provision dynamic, on-demand stacks without static templates
“KoMo closes the cloud skills gap by evolving self-service. Because it sees not just your code, but your running cloud, policies, and history, it generates Terraform that’s truly yours. That’s how enterprises finally get compliant self-service at scale.”
Turn Every Engineer into Your Best Engineer
KoMo transforms how teams deliver infrastructure by eliminating the skills bottleneck. Instead of relying on a handful of senior DevOps engineers to review every line, debug every error, or rewrite every plan, KoMo gives every contributor the context and confidence to ship infrastructure that meets enterprise standards.
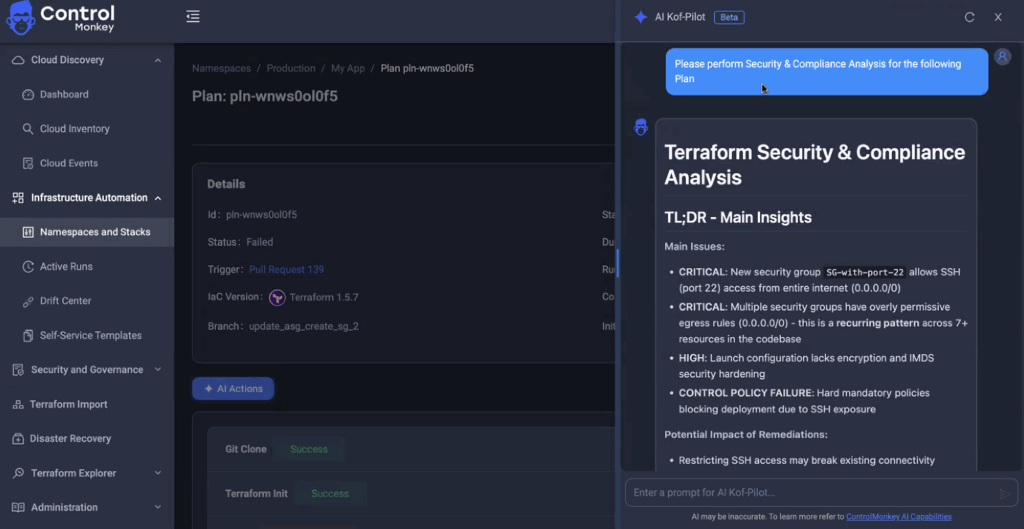
Real-World Uses for AI IaC Copilot
KoMo can answer the questions and requests that traditionally block engineers or overload DevOps experts:
- “Help me write Terraform to spin up a new service for periscope-app in dev using our naming conventions.”
- “Where do we use our S3 bucket module – and is it following best practices?”
- “Explain this Terraform plan in human-readable terms and flag risks.”
- “Analyze our Terraform/OpenTofu error and suggest a fix.”
- “Create a new-hire write-up of our Terraform layout: providers, modules, naming, and policies.”
- “Find references to Glue crawlers across repos and summarize the differences.”
- And many many more
See it in action?
Ready to turn every engineer into your best engineer? Explore AI IaC Copilot in our next Product Showdown