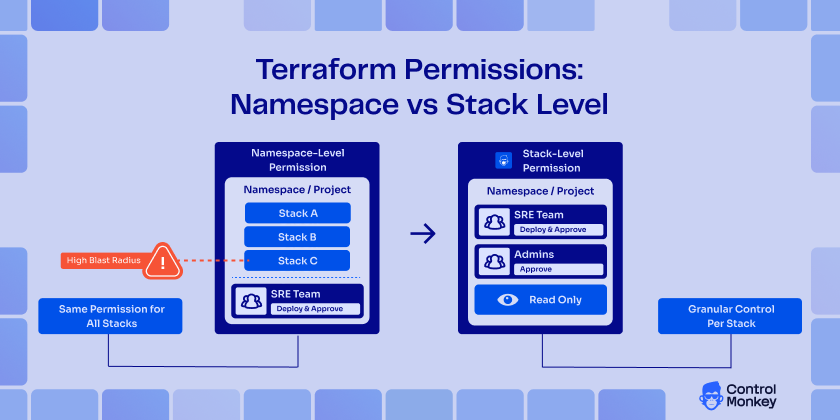
As Terraform workspaces grow, permission models that stop at the project or namespace level quickly become a challange. Critical production stacks don’t deserve the same access rules as everything else.
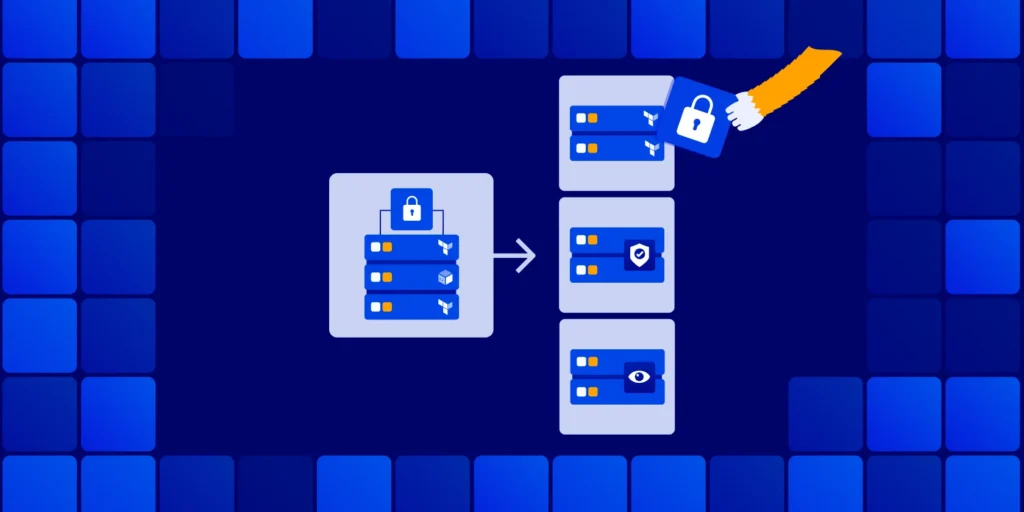
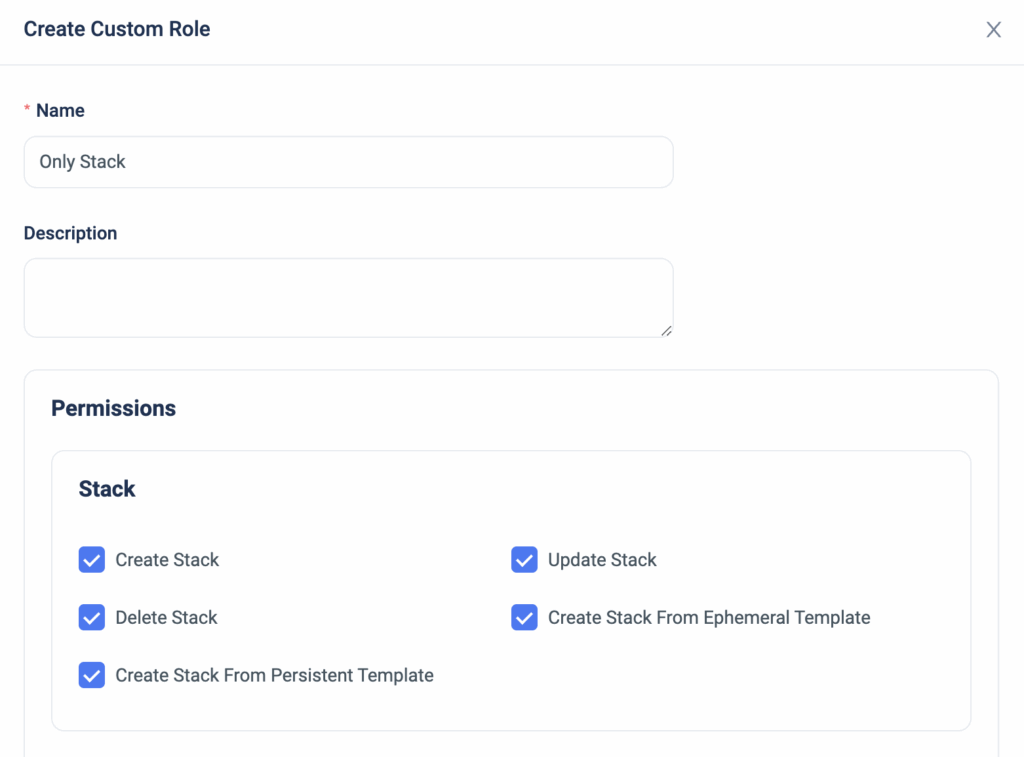
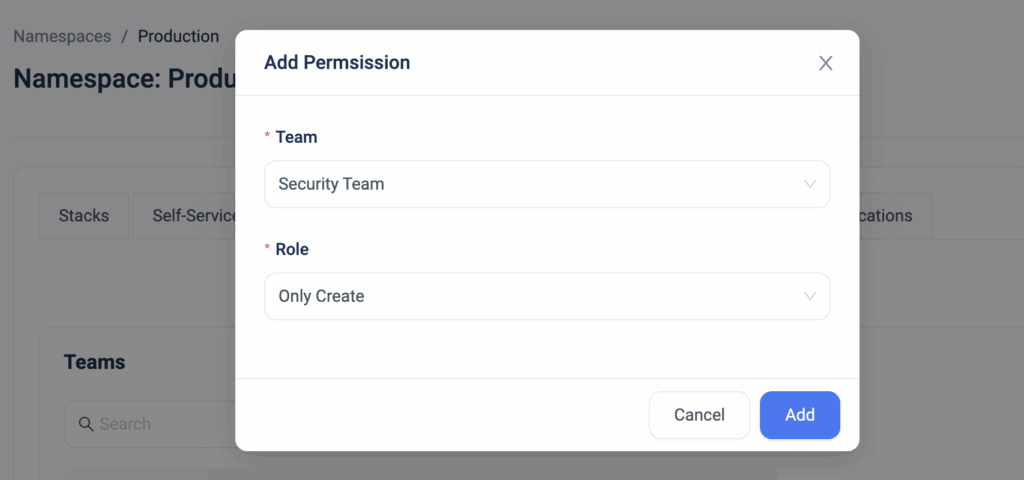
ControlMonkey now introduces Stack-Level Permissions, giving teams precise control over who can plan, deploy, and approve changes – down to the individual stack.
Introducing Stack-Level Permissions
Stack-Level Permissions extend ControlMonkey’s existing RBAC model beyond namespaces, enabling true enterprise-grade access control for Terraform environments.
What you can do:
- Assign permissions at the individual stack level, not just the namespace
- Limit high-risk actions (like deployment approval) to specific teams
- Map your IDP groups to ControlMonkey RBAC permissions
- Protect production and high blast-radius stacks without slowing delivery
- Maintain flexibility for DevOps and SRE teams across less sensitive stacks
Fine-Grained RBAC for Terraform Stacks / Precise Permissions for Complex Terraform Environments
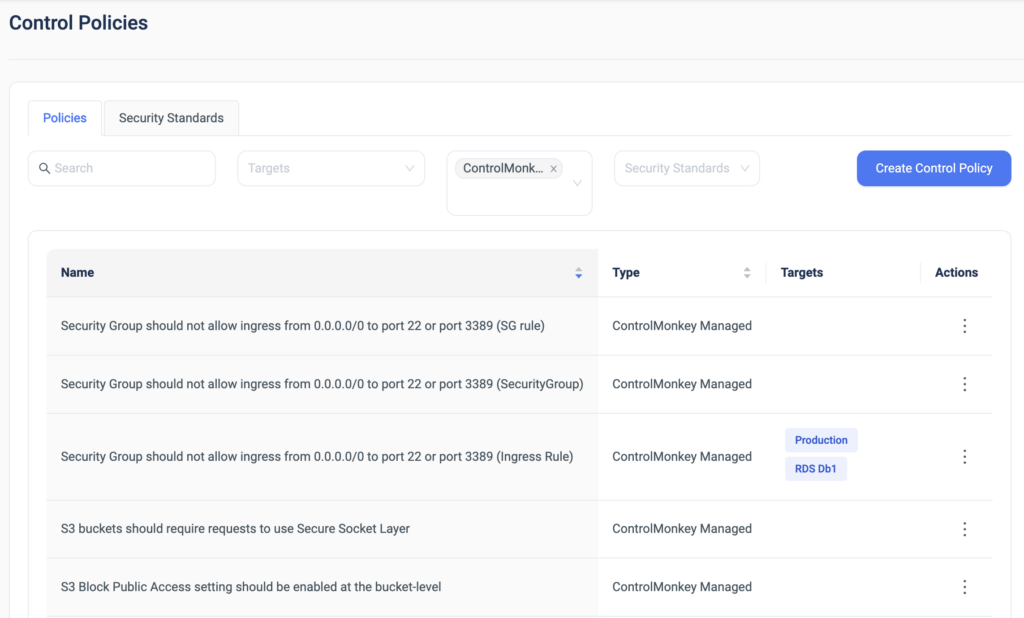
With Stack-Level Permissions, ControlMonkey closes a critical gap found in many Terraform Cloud alternatives.
This capability helps teams:
- Improve visibility into who can change what – and where
- Reduce operational risk by isolating sensitive stacks
- Strengthen IaC governance without introducing friction
- Scale Terraform safely, even as environments grow more complex
If you’re evaluating a Terraform Cloud replacement, granular permissions are not optional – they’re foundational.
Enterprise-Grade Permissions for Terraform Cloud Migrations
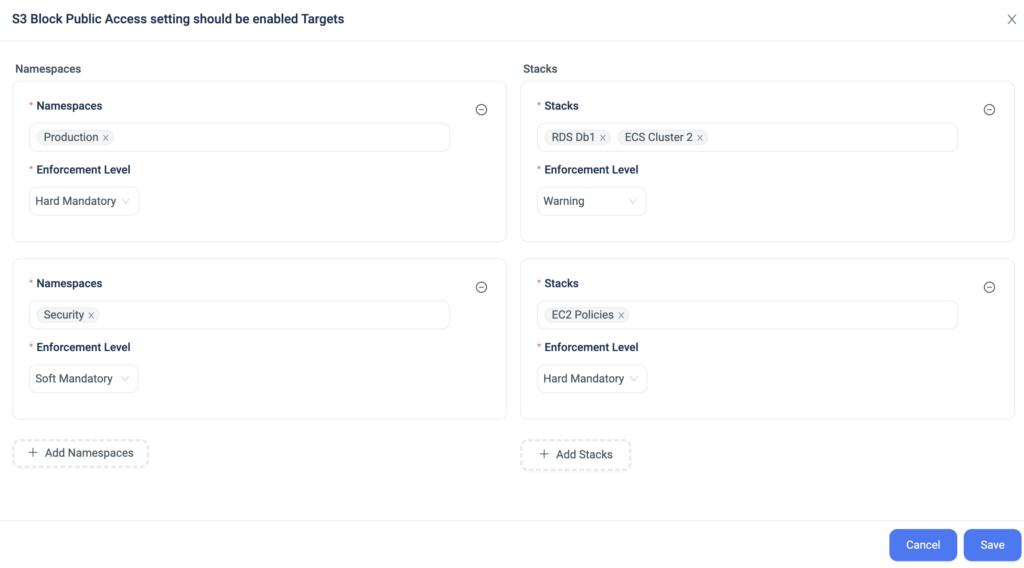
Terraform Cloud supports workspace-level permissions. When replacing it, the real question is whether you can enforce least privilege at the same granularity your production stacks demand.
ControlMonkey provides stack-level RBAC to isolate sensitive stacks while keeping delivery fast across everything else.
CTA: Ready to take control?
Explore Stack-Level Permissions and see why ControlMonkey is the most enterprise-ready Terraform Cloud alternative.