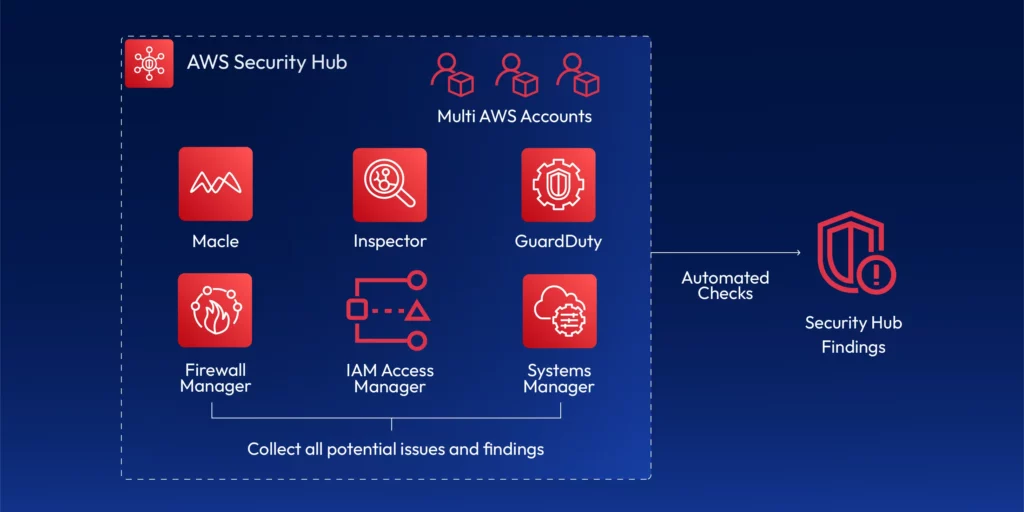
The transition to the cloud has also been accompanied by a growing need for effective cloud governance. While it brings benefits such as cost savings, flexibility, and scalability, it also introduces challenges. The planning for security, compliance, and governance in the cloud can become very difficult due to numerous services, infrastructure configurations, and regulatory requirements. AWS Security Hub is a central security tool that manages security across several AWS accounts and automates security checks. It is integrated dashboards show the current security and compliance status so that quick actions can be taken.
The idea is that it will aggregate alerts across multiple accounts through various services and partner tools. Such tools include:
- Guard Duty
- Inspector
- Macie
- IAM Access Analyzer
- AWS Systems Manager
- AWS Firewall Manager
- AWS Partner Network Solutions
AWS Security Hub consolidates all alerts into one centralized dashboard and collects all security findings in one place. You can act on the security alerts you receive. SecurityHub utilizes various AWS services and provides automated security auditing to ensure your cloud configuration complies with PCI-DSS, SOC 2, HIPAA, and more.
Cloud compliance and risk management are top priorities for all organizations. AWS Security Hub helps promote cloud governance. It focuses on cloud compliance and risk management. It empowers security teams to normalize processes, automate repetitive processes, and ensure that all configurations and resources comply with corporate policy.
Understanding AWS Security Hub
AWS Security Hub provides AWS customers and users with a single point where AWS customers have access to security findings and cloud compliance vulnerabilities across AWS accounts, services, and regions. It can detect cloud threats, analyze, and respond more quickly, staying ahead of threats and compliance standards.
Key Features of AWS Security Hub:
1. Centralized Dashboard:
Security Hub brings together findings from several AWS services. These include GuardDuty, AWS Config, AWS Inspector, and AWS Macie. You can view everything in one place. This would allow security operations to view security findings, compliance, and operational risk for all AWS accounts.
2. Cross-region Aggregation:
AWS Security Hub supports cross-region aggregation, simplifying centralized visibility. That means sending data from different regions in one central region makes security administration much easier.
3. Automated Compliance Checks with AWS Security Hub:
Security Hub checks the AWS environment for compliance with industry standards. These include the CIS AWS Foundations Benchmark, PCI DSS, SOC 2, and NIST. It also gives automated reports on compliance status.
4. Security Findings:
Security Hub gathers and aggregates AWS services and provides them with complete details like severity, resource name, and recommended remediation actions. It helps security teams determine which issues to address first.
5. AWS Organization Integration:
Security Hub has organization integration. That means you can manage all the security hub’s AWS accounts in one central account. Automatically, your organization adds new accounts. In that case, the security hub detects and adds them, and you can also have the management account by default as the security hub administrator. You can also design a member account as a designated delegated administrator for the security hub.
6. Custom Insights and Automation:
You can create custom insights within the Security Hub according to specific security or compliance frameworks. This is useful for companies with specific regulatory or security needs.
How AWS SecurityHub Works Across Services:
it gathers information from third-party products and other AWS services.
- GuardDuty identifies and warns against suspicious activity, such as odd traffic or unauthorized API activity.
- AWS Config monitors configuration changes and compliance with security policy.
- Amazon Inspector scans for vulnerabilities to analyze the security posture of an application.
Security Hub aggregates all these services’ findings, analyzes them for actionable insight, and places them within an easy-to-understand interface. Remediation steps are also available for all findings, such as updating security groups or patching vulnerabilities.
How AWS SecurityHub Controls Cloud Governance
Security and compliance within the mature AWS environment are difficult to enforce without a unified system for monitoring security and compliance. AWS Security Hub makes cloud management easier by acting as an always-on monitoring control plane that monitors the entire AWS environment for security and compliance issues.
How Security Hub Helps with Compliance Enforcement:
- Automated Compliance Assessments: it collaborates with AWS Config to perform automated compliance scans for industry best practices and regulatory compliance. Preconfigured security controls ensure your AWS setup is up-to-date and based on the newest cloud governance best practices.
- Enforcing Best Practices: Security Hub applies security best practices like CIS Benchmarks to scan your AWS account settings. For example, it checks whether you have turned on multi-factor authentication (MFA) for all IAM users or whether you have correctly configured security groups. It also utilizes best practices, such as least privilege access, by examining your IAM policy and suggesting improvements.
- Integration with Security Tools: Security Hub integrates with cloud security services such as AWS IAM to audit user permissions against adherence to the principle of least privilege. It also integrates with AWS CloudTrail to track user activity and catch potential governance anomalies in real-time.
- Security Alerts and Automation: Security Hub accumulates insights from multiple sources to assist in detecting vulnerabilities or misconfiguration. Security staff can automate remediation activities using AWS Lambda or Step Functions, which will be triggered upon detection. It significantly reduces the effort and provides more immediate responses to new risk findings.
Best Practices for AWS Security Hub
1. Enable Security Hub across all AWS accounts:
To monitor centrally, enable AWS Security Hub for all AWS accounts within your organization. AWS Organizations are used to structure accounts to aggregate security findings from all accounts.
2. Regularly Review Compliance Standards:
Regularly audit CIS AWS Foundations, PCI DSS, and NIST benchmarks to ensure your AWS configuration meets best practices. Use AWS Config Rules to scan and check compliance regularly.
3. Prioritized Key Findings:
Not all discoveries are created equal—Prioritize remediation by utilizing Security Hub’s severity levels: IAM roles facing the open Internet and old security patches require rectification.
4. Integrate Third-Party Solutions within Security Hub:
Security Hub can integrate third-party security products to present a typical security posture. Security hubs can consume data from 3rd party integrations and send data to other partners. For example,
- 3coresec
- Alert Logic
- Aqua
Security Hub integrates with services such as Atlassian, FireEye, and Fortinet to forward findings from Security Hub. For example,
- Atlassian
- FireEye
- Fortinet
Because this is where you manage your findings. Some of these 3rd party integrations can loop back into the security hub and update the findings. For example,
- Atlassian
- Service Now
5. Automated Remediation:
Use AWS Lambda functions to automate remediating Security Hub findings. For example, if a security group is misconfigured, AWS Lambda can update security group rules based on predefined actions.
6. Codify Infrastructure:
Use Infrastructure as Code (IaC) tools like Terraform to define and manage cloud resources consistently. This reduces manual misconfigurations, enforces policy-as-code, and enables drift detection when integrated with Security Hub and AWS Config.
Codifying Cloud Governance with Terraform
While AWS Security Hub provides critical detective controls for identifying misconfigurations, effective cloud governance starts earlier — at the infrastructure provisioning stage. This is where Infrastructure as Code (IaC) becomes essential.
Terraform, a leading IaC tool, enables teams to define cloud infrastructure in version-controlled configuration files. When paired with Security Hub and AWS Config, Terraform supports:
- Standardized provisioning across dev, staging, and production environments
- Enforcement of security policies by design
- Audit trails and version control for infrastructure changes
- Drift detection, ensuring infrastructure matches intended state
By integrating Terraform with security controls, organizations move from reactive detection to preventive governance — addressing misconfigurations before they happen, not after.
Integrating AWS Security Hub with Other AWS Services
1. Security Hub and AWS GuardDuty:
GuardDuty Generates findings, and these findings can be sent to the security hub. These findings are going to be converted to something called AWS Security Finding format (ASFF). GuardDuty dispatches these findings within 5 minutes, and then if you archive a finding in guard duty, it does not mean that it will update the finding in the security hub. Make sure you manage the findings directly in the security hub.
2. AWS Config Integration:
AWS Config regularly monitors the AWS resource configurations against security standards. Integrate Security Hub, receive combined compliance results, and initiate remediation actions automatically through the AWS Systems Manager.
3. Amazon Macie Integration:
Amazon Macie helps detect and protect sensitive information. Security Hub provides visibility of Macie results, such as exposure of Personally Identifiable Information (PII), and enables the organization to remediate them.
4. How Security Hub Works with IAM:
Security Hub integrates with IAM to assess the effectiveness of your policies. It scans for the use of least privilege access and notifies you of the presence of permissive roles or users.
Meeting Compliance Requirements
Security Hub helps companies follow important standards. These include PCI DSS, HIPAA, and SOC 2. AWS Security Hub checks AWS systems in real-time. This ensures that companies stay compliant with these standards.
Case Study Example:
A financial services company within the healthcare industry uses Security Hub for HIPAA compliance. It scans its AWS environment regularly for HIPAA compliance, such as encrypting protected data at rest. It encrypts AWS storage buckets to keep data at rest. Security Hub tracks and logs all such recommendations so the company can achieve compliance with minimal risk of human error.
TL,DR:
AWS Security Hub, a visionary compliance and security solution, actively addresses increasingly complex cloud configurations and stringent compliance needs. Security Hub works well with many AWS products. It helps create a single command center to manage, govern, and secure cloud environments.
Organizations can avoid security risks and maintain compliance across the cloud environment through continued automation, centralized security monitoring, and forward-thinking governance. As cloud governance continues to grow, AWS Security Hub will lead in helping businesses with compliance. It offers an easy way to manage security and keeps companies informed about the latest industry standards.
Take the next step in simplifying your cloud governance. With ControlMonkey, you can automate Terraform deployments, enforce policy-as-code, and manage AWS Security Hub findings from a single platform. Book a demo to see how ControlMonkey can help you scale compliance and governance with confidence.