If you’re diving into OpenTofu to manage your infrastructure, you’re in for a treat—it’s powerful, flexible, and open-source without the vendor lock-in. But with that flexibility comes complexity, and even small missteps can lead to critical OpenTofu errors in production.
What Are the Most Common OpenTofu Errors?
As I meet with customers and prospects, I hear more and more teams expressing concerns about vendor lock-in. Many are migrating to OpenTofu—and while that’s a smart move, it often introduces a new set of challenges. Not because teams lack expertise, but because scaling Infrastructure as Code always comes with edge cases that are easy to miss.
In those conversations, five errors come up again and again. These aren’t rare bugs—they’re common issues that even mature teams run into. If you’re running OpenTofu in production, these are the ones I recommend watching out for:
The Top 7 OpenTofu Errors DevOps Teams Should Watch For:
- Provider Version Conflicts – Mismatched or misreferenced provider blocks that break deployments.
- Misconfigured Backends – Using local state or skipping locking, leading to lost or inconsistent state.
- Poor Module Structure – Monolithic modules, inconsistent file layout, and hardcoded values.
- Variable Mismanagement – Missing defaults, no validation, and unclear naming.
- Environment Drift and Workspace Sprawl – Manual changes, untracked environments, and hidden infrastructure risk.
Let’s break each one down—and how to fix them before they become blockers.
🟨 Related OpenTofu & Errors:
- 📘Terraform Errors Guide – A breakdown of common Terraform issues and how to fix them fast.
- 🌍OpenTofu Multi-Cloud Guide – Best practices for using OpenTofu across AWS, Azure, and GCP.
1️⃣ Provider Version Conflicts
Provider version mismatches or redundant provider blocks can cause conflicts. Maybe you’ve got one module pulling aws ~> 4.0 and another demanding aws ~> 5.0. Or worse, you accidentally reference the Terraform registry with fully qualified provider names.
terraform {
required_providers {
aws = {
source = "registry.terraform.io/hashicorp/aws"
version = "~> 5.0"
}
}
}OpenTofu recognizes provider addresses in the format hostname/namespace/type where hostname resolves by default to registry.opentofu.org which is the public OpenTofu repository when using OpenTofu. However, if you are migrating from Terraform, you may have defined the hostname as registry.terraform.io, which explicitly points to Terraform Registry, which violates the T&C of Terraform Registry when used with OpenTofu.
How to Avoid Provider Errors in OpenTofu
- Reference OpenTofu Registry: Remove references to the Terraform registry with fully qualified provider or module names. Stick to the OpenTofu registry instead. However, you can use third-party registries based on your requirements.
- Lock Versions: Pin your provider versions in the required_providers block. Here’s a quick example:
terraform {
required_providers {
aws = {
source = "opentofu/aws" # hashicorp/aws works as well
version = "5.0.0"
}
}
}- Use shared provider configurations: To make the modules portable, it is best practice to define the provider configurations within your configuration instead of within the module itself. Let’s look at an example;
You can use an alias in the provider block to manage multiple provider configurations. This comes in handy when you want to deploy to multiple regions.
Root Module:
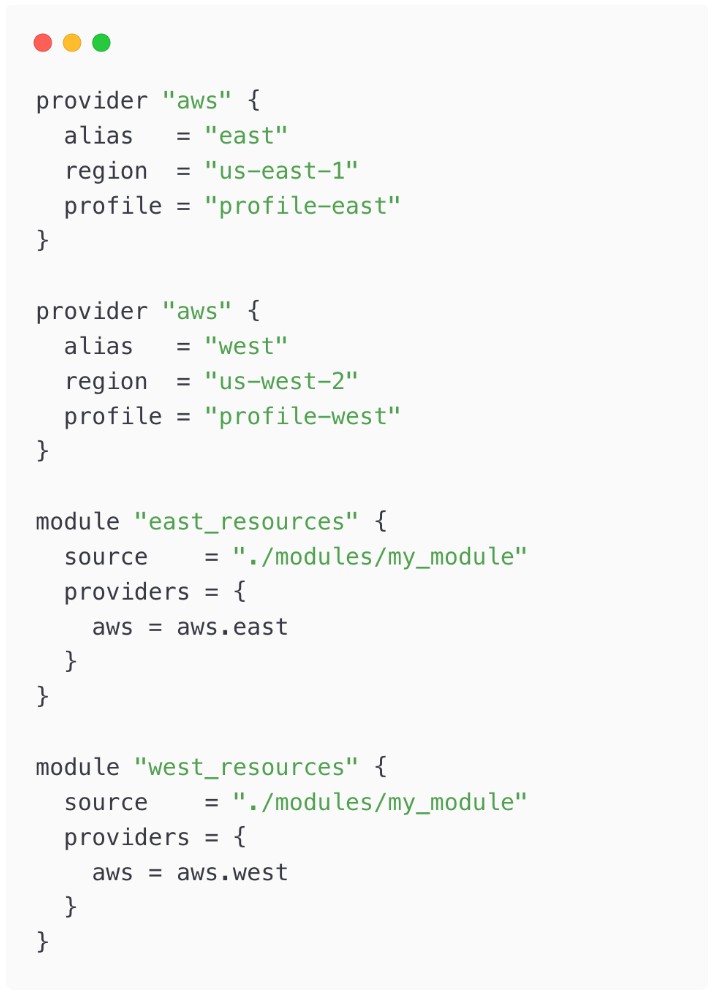
Child Module:
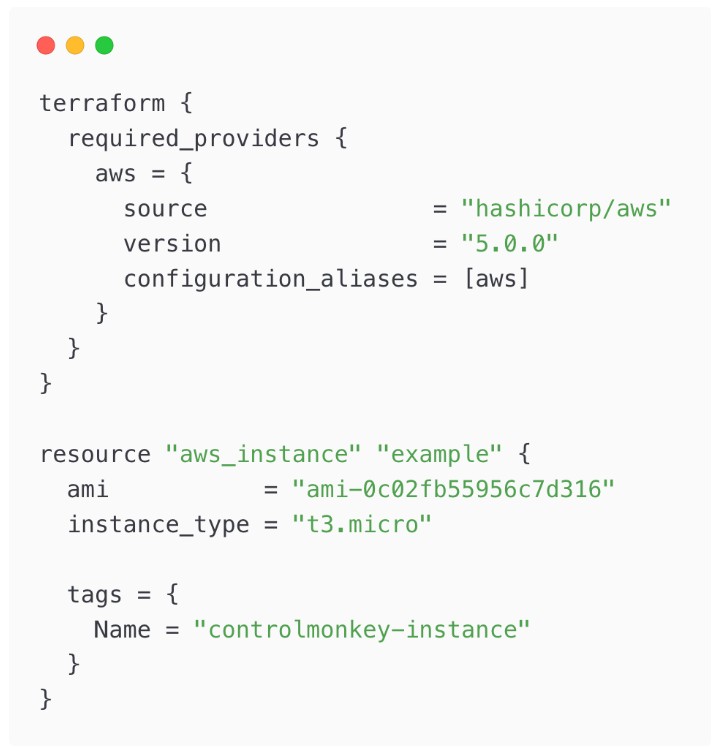
2️⃣ Remote State and Locking Best Practices
The state file is OpenTofu’s memory of your infrastructure. OpenTofu uses the state file to track resources created and plan changes when OpenTofu configurations change.
One of the most common mistakes is developers starting with using a local state. Local state files get lost, overwritten, or cause conflicts in team settings. Another mistake is not enforcing a locking mechanism for the state.
Remote State and Locking in OpenTofu
- Use remote state with locking: Use a remote backend like S3 or a vendor-neutral backend with locking to keep things consistent. Here is an example of an OpenTofu backend with S3 native locking (Supported from v1.10.0 onwards)
terraform {
backend "s3" {
bucket = "controlmonkey-state-backend"
key = "statefile"
region = "us-east-1"
encrypt = true
use_lockfile = true
}
}- Implement access control: You need to manage who has access to the state file and, by extension, control who can execute terraform against your infrastructure with the state file. Your state may contain sensitive data. If using AWS S3, you can use IAM Policies to manage access.
3️⃣ Module Mistakes with Module Design
Modules should be well structured to make your OpenTofu code scalable and manageable.
A few of the most critical mistakes are;
- Creating monolithic or “god modules”, which try to provision an entire application. Monolithic modules cause tight coupling between resources, which is hard to test and debug.
- Poor and inconsistent file structures. In one module, there are separate files for different concerns (variables.tf, main.tf, output.tf ), but in another module, everything is written in the main.tf .
- Mixed abstraction levels within a module. Mixing low-level infrastructure (like individual security group rules) with high-level concepts (like complete applications) within the same module creates confusion and reduces reusability.
- Using hardcoded values in modules reduces reusability.
Avoiding OpenTofu Errors with Module Design
- Follow the Single Responsibility Principle: Modules should focus on doing one thing well. For example, separate your networking, compute, and database modules.
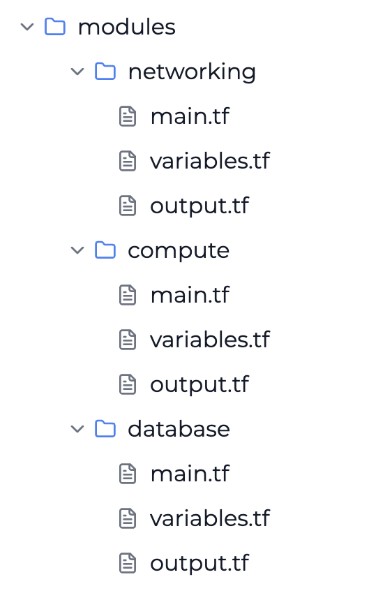
- Be consistent with file naming and structure: main.tf for resources, variables.tf for inputs, outputs.tf for outputs, and versions.tf for provider requirements.
- Parameterize modules: You can refer to the variable instead of hardcoding within the module.
# Root Module (./main.tf)
module "web_server" {
source = "./modules/compute"
instance_type = "t2.micro"
}
# Compute Module (./modules/compute/main.tf)
resource "aws_instance" "web" {
instance_type = var.instance_type # Refer the instance type
# Other Configurations
}4️⃣ How to Prevent Errors in OpenTofu Variable Usage
Unclear or conflicting variable inputs lead to confusion. Without defaults or validation, someone might pass a bad value (or nothing), and your deployment crashes. When working with variables, you should always follow best practices.
# Confusing variable definitions
variable "x" { # Unclear name
type = string
}
variable "count" { # Conflicts with built-in
type = number
}How to Prevent Errors in OpenTofu Variable Usage
- Use descriptive, consistent naming conventions
- Provide sensible default values for your variables
- Implement input validation rules
- Group related variables in a single file for clarity (Best practice: use variables.tf)
Here is a well-defined variable with sensible defaults and validation:
variable "instance_type" {
type = string
default = "t3.micro"
description = "EC2 instance type for the web server"
validation {
condition = contains(["t3.micro", "t3.small"], var.instance_type)
error_message = "Instance type must be t3.micro or t3.small."
}
}5️⃣ Preventing Drift in OpenTofu Environments
As your infrastructure grows, it’s easy to lose track of different environments and workspaces. Untracked workspaces or drifting environments can spiral out of control. You end up with a prod workspace that is different from actual deployment or a dev environment no one remembers creating.
The drifts can happen when developers make hotfixes directly from the console or APIs. Untracked workspaces also lead to orphaned resources and deployment issues that are hard to debug.
Preventing Drift in OpenTofu Environments
- Use clear workspace naming: Have a pattern such as <environment-name>-<region> when you create workspaces. Example: tofu workspace new prod-us-east-1
- Automate deployments with CI/CD pipelines to enforce consistency.
- Use drift detection tools: OpenTofu’s tofu plan is a good starter. You can adopt tools such as ControlMonkey for advanced drift detection and remediation.
if you reached this far – Find Free Downloadable PDF Version
-
5 OpenTofu Errors and how to fix them →
– Downloadable version
6️⃣ Module Registry Conflicts – Wrong Source
One of the most common mistakes we see during OpenTofu migrations is teams continuing to reference the Terraform Module Registry. They use fully qualified module names like hashicorp/vpc/aws out of habit – and that’s a problem. Incorrect module references lead to failed runs, missing dependencies, or license violations that block production workflows.
The risk of referencing Terraform modules breaks compatibility with OpenTofu. This causes failed runs, unresolvable dependencies, and governance issues.
How to Fix It
- Audit all module source paths. Replace terraform.io or hashicorp/ sources with OpenTofu-compatible ones.
- Host your own module registry or pull from registry.opentofu.org or a third-party OpenTofu-compliant registry.
- Use relative paths (e.g., ./modules/vpc) where possible to reduce external dependencies.
7️⃣ Legacy Pipelines Still Use the Terraform Binary
You’ve moved to OpenTofu, but some of your automation hasn’t. Legacy CI/CD pipelines, GitHub Actions, or container builds may still be calling terraform—even if your team thinks they’ve switched. Terraform has been the default for years. It’s easy to miss places where the binary is still being referenced, especially in older scripts or infrastructure tooling.
You think you’re running OpenTofu, but in reality, some environments are still using Terraform. This leads to inconsistent behavior, misaligned state, and audit failures.
How to Fix this OpenTofu mistake?
- Check all automation (CI configs, scripts, Dockerfiles, runners) for the word terraform.
- Replace with tofu and verify versioning is consistent across environments.
- Validate by outputting the tofu version during every run.
Conclusion: How to Avoid OpenTofu Errors
There, you will find five common OpenTofu mistakes and how to avoid them. Lock your providers, set up remote backends, structure modules correctly, manage variables carefully, and keep your environments consistent. You’ll build robust, scalable OpenTofu workflows.
OpenTofu gives you freedom – but ControlMonkey gives you control. Book a demo to see how we help teams eliminate errors, reduce toil, and accelerate delivery with automated OpenTofu governance.
Version History:
- 30.6.2025 – Original publication date
- 02.07.2025 – Two new Errors and Mistakes added
- 02.10.2025 – PDF Addition





