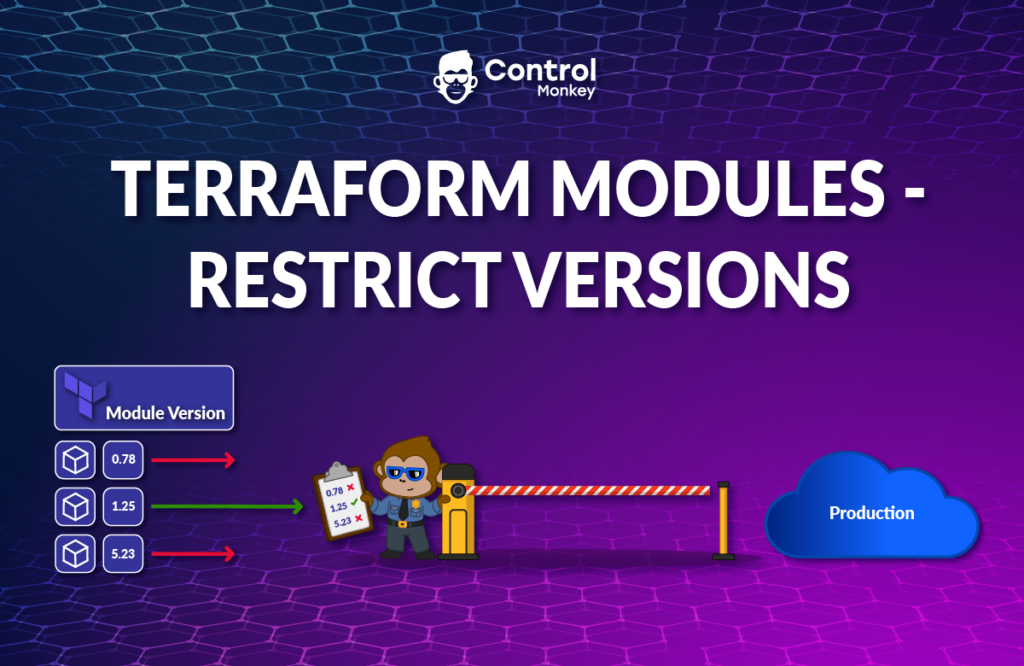
Terraform Modules are a great way to reduce the amount of code engineers write for similar infrastructure resources and are considered an efficient way to replicate cloud services across environments.
An essential aspect of using modules is versioning, which enables cloud teams to systematically release module upgrades. This ensures the use of a more secure and compliant infrastructure by keeping the modules up-to-date.
However, controlling strictly which Module versions and sources engineers are allowed to use becomes a massive challenge at scale.
An everyday use case is if, for example, I upgrade a few of my Terraform Modules with extra security measures and want to ensure that engineers are using the latest version.
To tackle this challenge, we proudly announce the latest enhancement to our Terraform CI/CD engine, Terraform Modules – Restrict Versions control policies.
ControlMonkey users can now easily create Control Policies that allow or restrict Terraform Modules Sources or Versions as part of the Infrastructure CI/CD.
Terraform Modules – Restrict Versions consists of 3 types of policies:
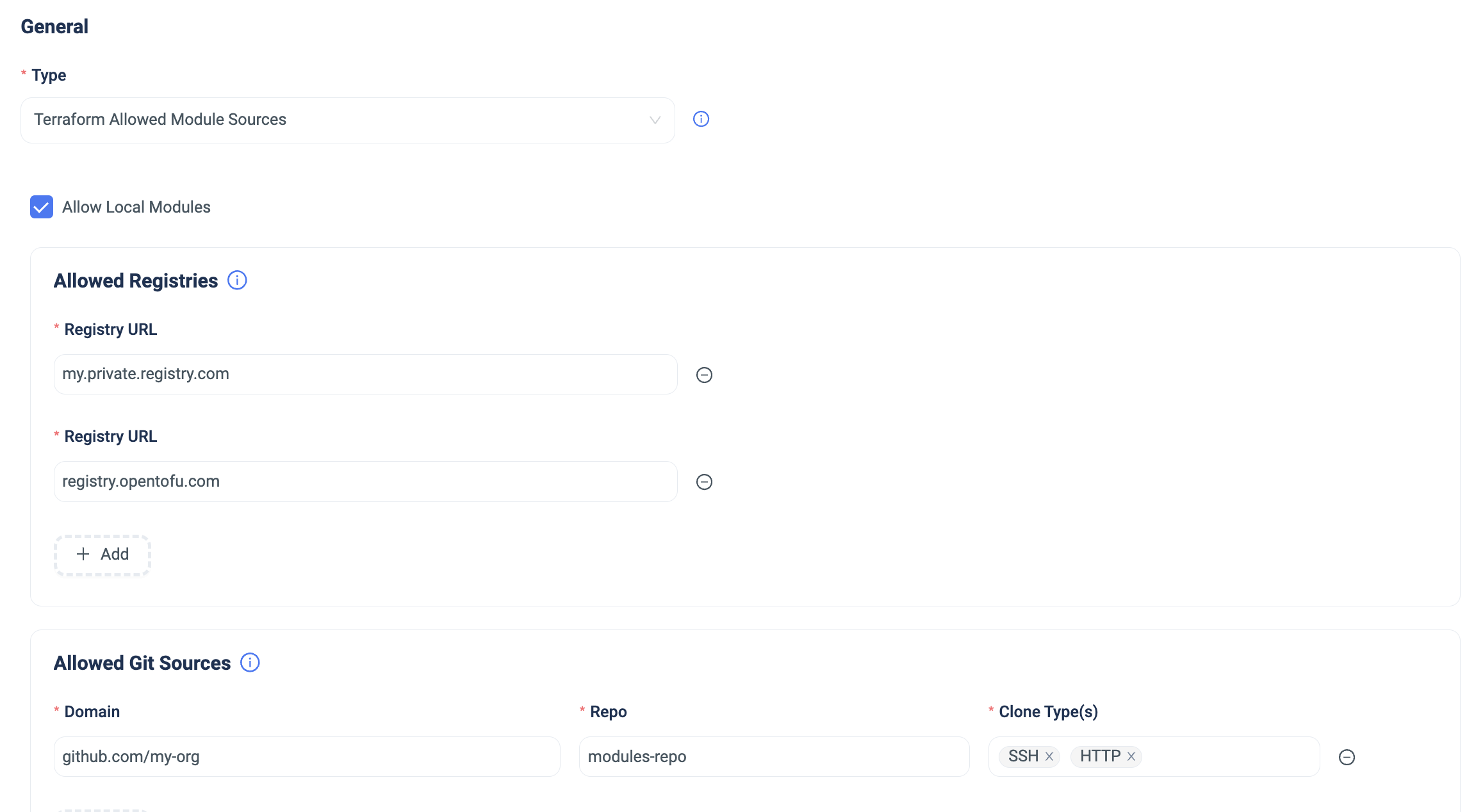
Terraform Allowed Module Sources Policy
This policy enforces that all the Terraform Modules used in the code reside in a pre-approved Registry or an organization’s GitHub repo.
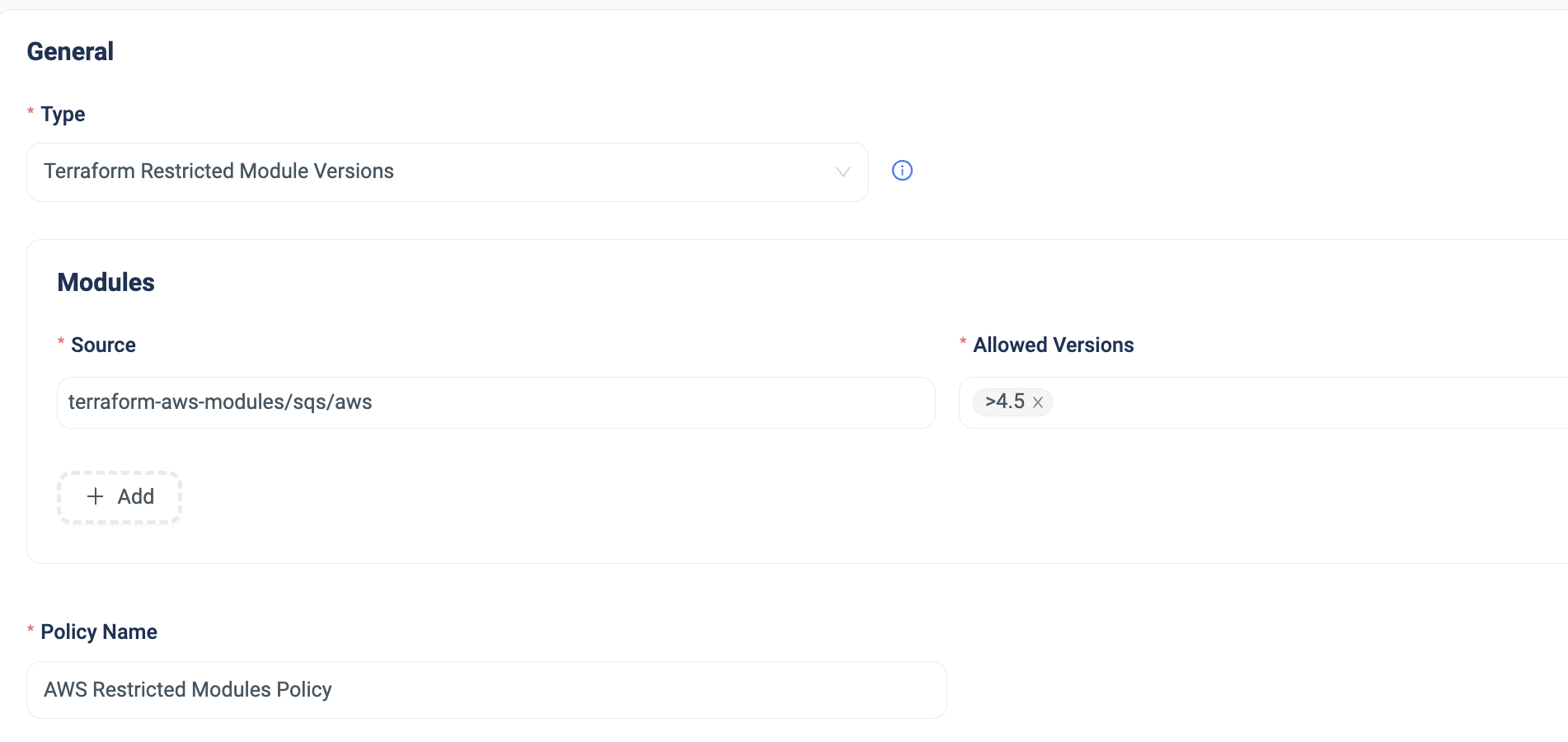
Terraform Restricted Module Versions Policy
This policy enforces the Terraform Modules versions that can be used in the code.
The value can be a specific version, a range of versions, or from a particular version and above.
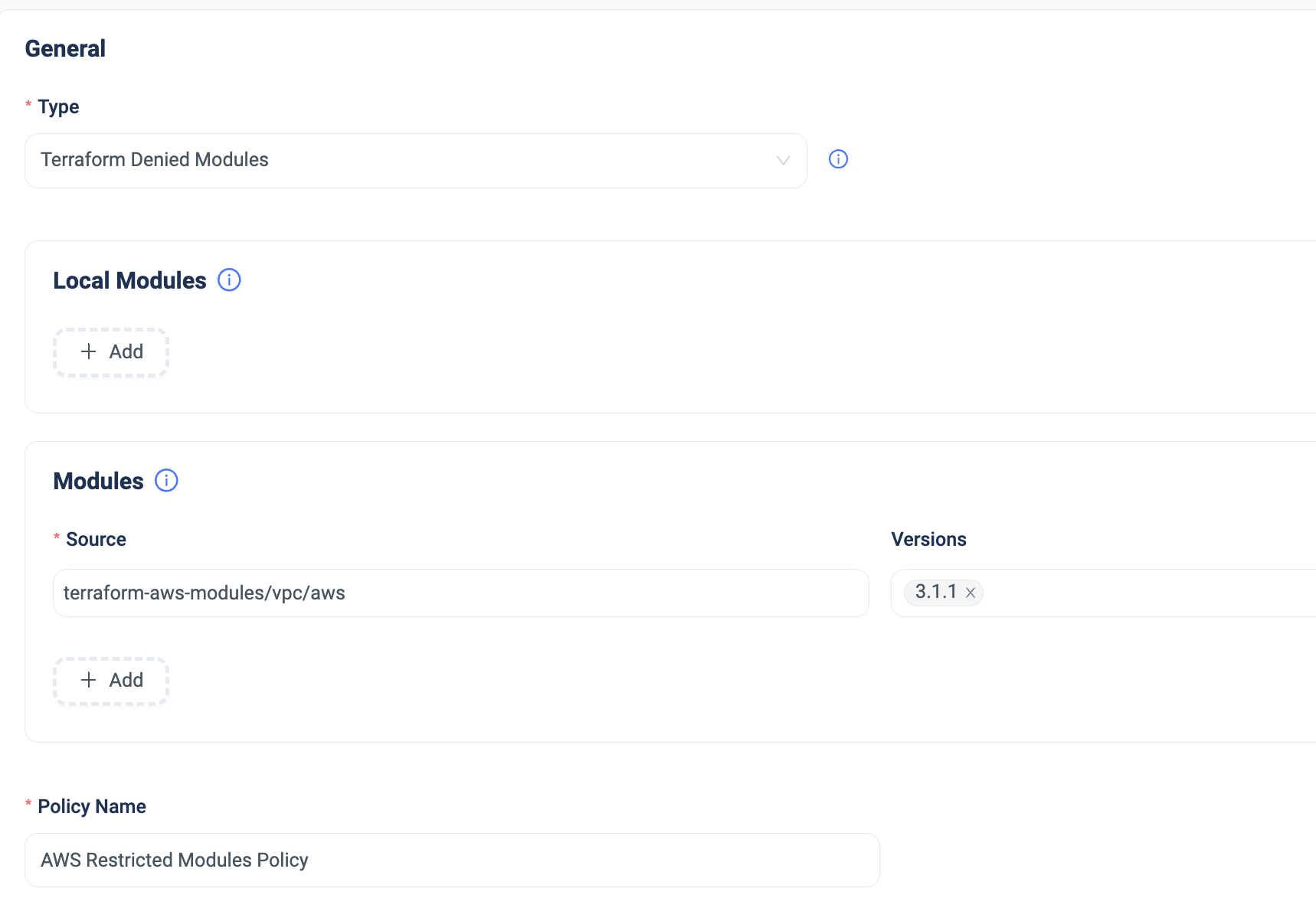
Terraform Denied Modules Policy
This policy ensures that Terraform Modules from unauthorized sources are not used.
For instance, if there is a folder in your Git repository containing legacy modules that should not be used, you can designate these as ‘Denied.’ This provides immediate feedback to all users, preventing accidental usage
Summary
In case one of these policies is violated, ControlMonkey will warn the user who issues a PR that either their Terraform Module version is outdated, the Terraform Module path they are trying to use is restricted, or the specific Terraform Module they wish to use is restricted.
Managing and Governing Terraform Modules at scale is a massive challenge for infrastructure teams and, in some instances, poses a risk to the organization.
With ControlMonkey, you can create policies that strengthen your control over Terraform Modules and ensure they remain an efficiency driver rather than an operational burden with just a few clicks.
Are you looking for the best way to stay on top of your Terraform Modules?
Our Terraform experts can’t wait to show you around.