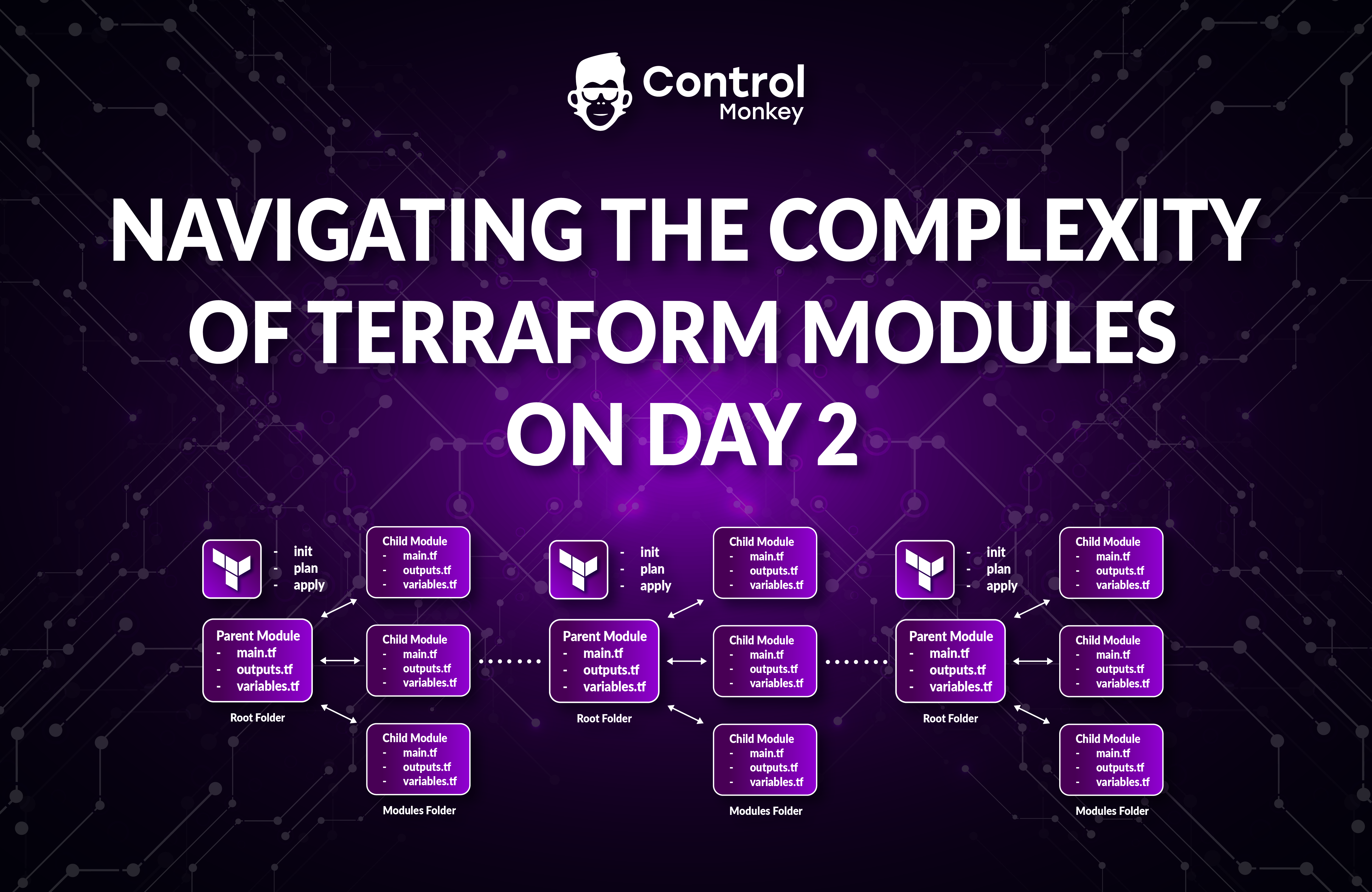
Day 2 of managing your Terraform infrastructure can often feel like navigating through a labyrinth. Initially, setting up your infrastructure as code (IaC) with Terraform modules might seem straightforward. However, as your codebase expands and you start utilizing multiple Terraform modules across various projects, the complexity multiplies. This situation becomes even more challenging when the team members who originally wrote your Terraform code or structured your Terraform repositories are no longer with the organization. Suddenly, you’re left with a sophisticated puzzle of code and modules, with little to no guidance on how it was all meant to work together. At this juncture, keeping your code under control and enforcing consistent use of modules throughout your projects isn’t just a best practice—it’s a necessity.
As your organization’s Terraform environment grows, you may find yourself asking critical questions: How can we manage multiple modules across different repositories efficiently?
How do we maintain visibility into who uses what and where?
What versions of each module are we using, and how do we ensure they are up-to-date yet stable?
More importantly, how do we enforce the use of approved registries or module sources to maintain security and compliance standards?
This blog post aims to untangle these complexities, offering strategies and practices to manage your Terraform modules effectively. By implementing these measures, you can ensure that your Terraform infrastructure remains robust, scalable, and manageable, even in the absence of its original architects.
Visibility: Who Uses What and Where
One of the first questions that arises when managing a complex structure of Terraform modules and repositories is, “What Terraform modules are being used, and where?” This question becomes particularly pressing in two scenarios:
- When planning to upgrade a Terraform module: You’ll need to know all the places within your Terraform repositories where the module is being used to assess the impact of the upgrade.
- When compiling an audit report: For compliance or security reviews, you may need to provide a list of all the open-source components you’re using, essentially creating a Software Bill of Materials (SBOM) for your Terraform modules.
To address these needs and achieve the necessary level of visibility, we recommend the following strategies:
- Implement Module Catalogs: Establish a centralized module catalog that inventory all available modules, including their versions and usage instructions.
A module catalog not only streamlines module discovery and adoption but also serves as a critical resource for tracking module versions and dependencies across projects. - Use Dependency Graphs: Leverage the ‘Terraform graph’ command to visualize how modules depend on each other. This graphical representation can be invaluable for understanding complex interactions between modules and for identifying potential issues when planning module upgrades or changes. Dependency graphs offer a clear overview of module relationships, making it easier to pinpoint where specific modules are used and how they contribute to the overall infrastructure.
- Adopt Code Search Tools: Use code search tools across your repositories to find instances of module usage. This can help in identifying which projects are using specific modules. Major version control system vendors, such as GitHub, GitLab, Bitbucket, etc typically provide built-in capabilities for searching within repositories.

Managing Versions: Ensuring Stability and Consistency
Keeping track of the versions of modules used throughout your codebase is crucial. This vigilance allows you to identify outdated modules, as well as ensure you can retire specific versions with confidence, knowing they are no longer in use. To maintain this level of control and visibility, consider the following strategies:
- Semantic Versioning: Implement semantic versioning for your modules to communicate changes and compatibility. This approach is inherent in module registries, providing a structured way to manage versioning automatically. For those utilizing private, Git-based repositories, tagging your versions is a practical method to adopt semantic versioning manually. This practice facilitates clear communication about updates and backward compatibility, simplifying the decision-making process for module upgrades.
- Module Version Constraints: Within your Terraform configurations, it’s essential to use version constraints. These constraints help prevent the automatic incorporation of updates that might disrupt your infrastructure’s stability. When sourcing modules from private Git repositories, make sure to specify the version using the ‘ref’ query parameter. This precision ensures that you always know which version of a module your infrastructure will deploy, mitigating the risk of unexpected changes.
- Versions Usage Tracking: Expand your Module Usage Catalogs to not only list the modules’ usages within your code but also track each usage instance’s version constraint and the actual version determined by that constraint.
This comprehensive tracking ensures a clear overview of which versions are actively in use across all projects. Such detailed records become invaluable when planning module updates or retirements, as they allow you to pinpoint exactly where and how each version is employed within your infrastructure.
Enforcing Registries or Terraform Module Sources
One critical aspect to carefully manage is the prevention of utilizing compromised or unauthorized module sources.
Unauthorized sources can range from an employee using modules from their own private Git repository to the use of public module registries contrary to organizational policies that mandate the use of private registries exclusively. Such practices expose your infrastructure to significant security risks and compliance violations. To mitigate these risks, consider adopting the following approaches:
- Periodic Code Scans: Regularly scan your Terraform codebase to identify and rectify instances where module sources do not align with your organization’s rules and guardrails. This detective measure ensures ongoing compliance and security by promptly detecting and addressing deviations from established policies.
- Integrate ‘Module Source’ Checks in Terraform CI/CD Pipelines: Embed checks for module sources directly into your Terraform Continuous Integration/Continuous Deployment (CI/CD) workflow. This integration provides immediate feedback to engineers about the compliance of their chosen module sources. For enhanced enforcement, consider implementing these policies in a ‘hard-mandatory’ mode. This approach ensures that any attempt to introduce non-compliant code into the codebase triggers the CI/CD process to cancel the build automatically, thus preventing potential compliance issues from reaching production environments.
Ensuring New Resources Are Using Your Terraform Modules
One last crucial aspect of maintaining a secure and compliant infrastructure with Terraform involves ensuring that all/some resources are provisioned using your organization’s approved modules.
For instance, if your organization has developed a specific module for provisioning S3 buckets, team members must utilize this module instead of directly using the aws_s3_bucket Terraform resource. Bypassing the approved module and directly creating resources can lead to security vulnerabilities and compliance breaches. To mitigate this risk and ensure uniformity in resource creation, the following measures are recommended:
- Policy Enforcement in CI/CD Pipelines: Integrate policy checks within your Continuous Integration/Continuous Deployment (CI/CD) pipeline to enforce the exclusive use of approved modules for resource creation. This step ensures that any attempt to deploy resources outside of the defined modules is automatically detected and blocked, maintaining compliance and security standards.
- Codebase Scanning for Direct Resource Usage: Regularly scan your Terraform codebase to identify instances where “plain” resources are being used instead of the designated modules. This proactive approach helps in quickly pinpointing deviations from your organization’s module usage policies.
- Education and Documentation: Foster a culture of compliance and security by providing comprehensive documentation and training focused on the importance of using approved modules. Ensuring that your team understands the rationale behind these guidelines and how to properly use the modules will foster adherence and minimize the risk of non-compliant resource provisioning.

Summary
Terraform modules play a crucial role in ensuring the repeatability and security of your infrastructure. However, as your Terraform codebase expands, managing these modules can become increasingly complex. Throughout this blog, we have explored various challenges that arise with module management and provided strategies to effectively address them.
For some, the solution lies in developing custom tools tailored to their specific needs. Others, however, may seek ready-made solutions that can seamlessly integrate into their existing workflows. For those in the latter group, ControlMonkey’s ‘Terraform Modules Explorer’ offers a compelling answer to the challenges discussed. ControlMonkey’s Terraform Modules Explorer capability is designed to provide comprehensive visibility and control over your Terraform modules, ensuring that you can manage your infrastructure with confidence and efficiency.
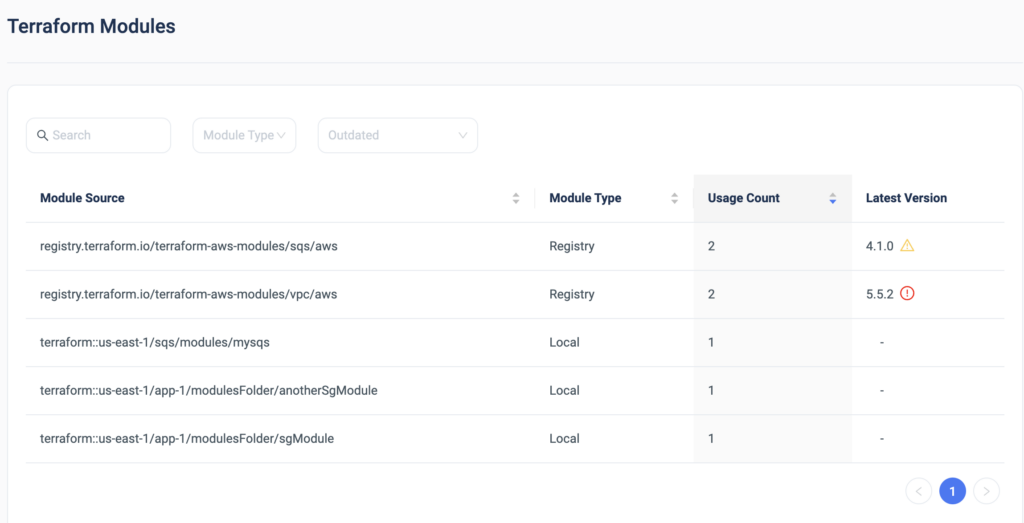


Whether you’re building your solutions or leveraging tools like the ControlMonkey, the key is to approach Terraform module management with a strategic mindset. By doing so, you can maintain a secure, compliant, and repeatable infrastructure that scales with your organization’s needs.