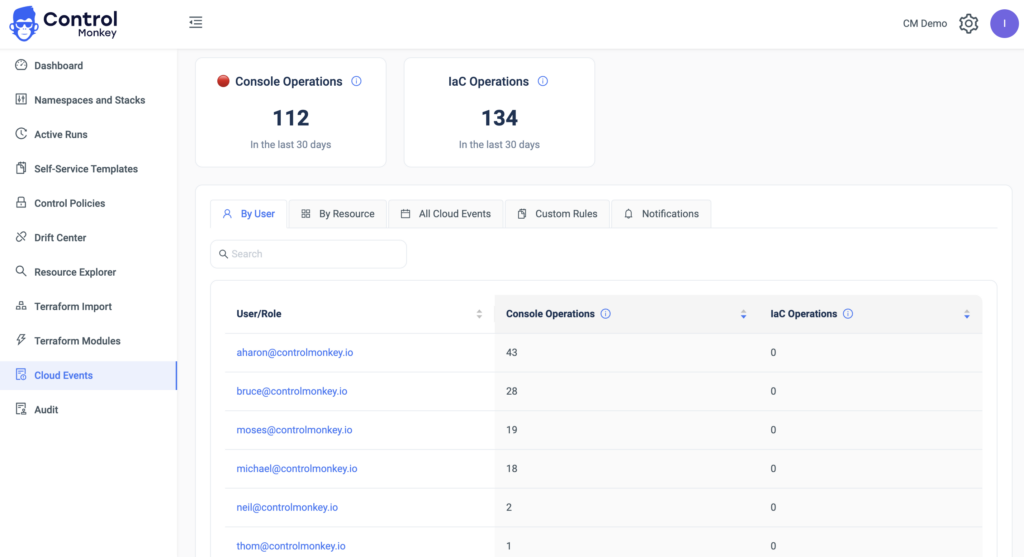
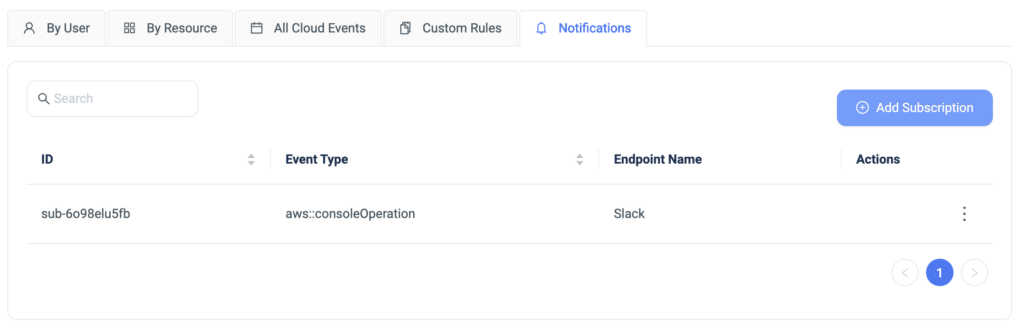
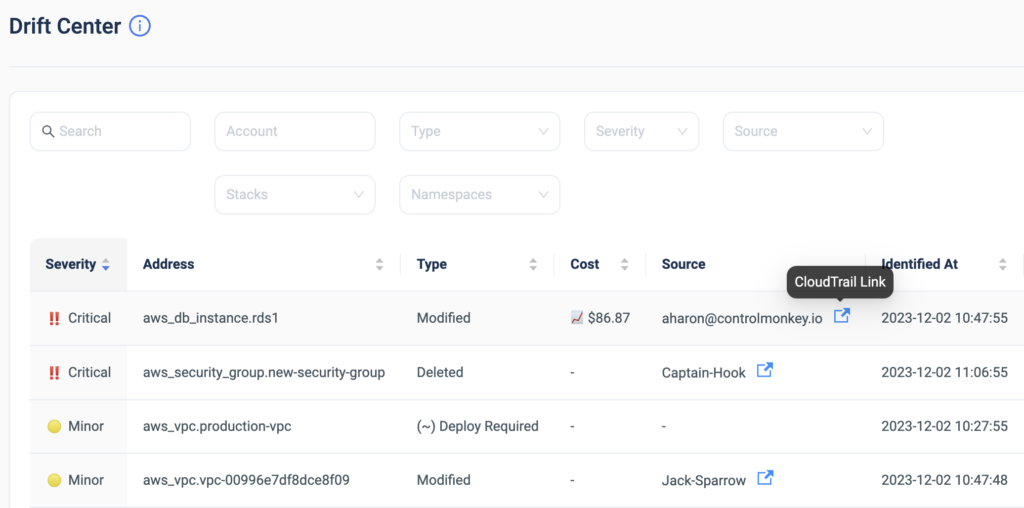
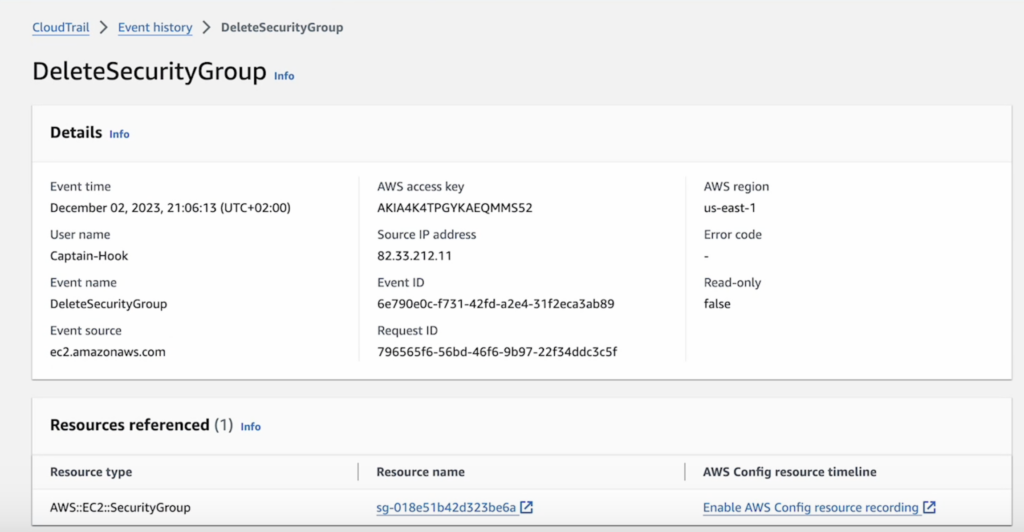
Last month we released the feature ‘Console Operations Notifications’, which notifies ControlMonkey users whenever someone performs operations from the AWS console.
The feedback we got from our customers was outstanding, but some of them also indicated that there are certain actions that they allow their teams to perform in the AWS console, so they wanted to have a mechanism to allow-list those actions that are permitted in their organization.
So to support this request we have developed a new capability, ‘Allowed Console Operations’.
‘Allowed Console Operations’ enables ControlMonkey users to define rules for specific actions that are permitted to be performed in the AWS console.
For example: Updating Lambda function code from the AWS console.
This feature’s granularity allows ControlMonkey users to apply the rule to a specific account, region, resource name, or resource type.
To make things easier, we have also added the option to create an allowed console operation rule directly from a console operations event in our cloud events dashboard, in 2 clicks.
While our vision is enabling our customers to minimize their ClickOps in the AWS console, this capability adds that extra layer of customization which allows them to also reduce unnecessary ClickOps and also the notifications for permitted actions.